In today’s rapidly evolving digital landscape, safeguarding your organization’s valuable data and ensuring secure access for employees and partners are paramount. Microsoft Entra ID, a powerful cloud-based identity and access management (IAM) service, provides a comprehensive solution to these critical challenges. This blog post will guide you in understanding Microsoft Entra ID, exploring its key features and benefits, and providing a step-by-step tutorial to help you effectively leverage its capabilities. Whether you’re a security professional, IT administrator, or simply interested in enhancing your organization’s security posture, this comprehensive resource will equip you with the knowledge and practical guidance needed to implement and manage Microsoft Entra ID effectively.
What is Microsoft Entra ID?
Microsoft Entra ID is a comprehensive cloud-based identity and access management (IAM) service that empowers organizations to securely manage user identities and control access to resources across diverse environments. By using cloud-based infrastructure, Entra ID provides a centralized platform for managing user accounts, enforcing strong authentication mechanisms such as multi-factor authentication (MFA), and implementing granular access controls through features like Conditional Access. This enables organizations to enhance security, improve user productivity, reduce operational overhead, and ensure compliance with industry regulations. Key capabilities include Single Sign-On (SSO) for seamless application access, identity protection capabilities to detect and mitigate threats, and seamless integration with a wide range of applications and services within and beyond the Microsoft ecosystem.
It offers:
- Comprehensive Identity and Access Management: Microsoft Entra ID empowers organizations to secure and streamline their operations with a robust cloud-based identity and access management solution. It seamlessly connects employees, customers, and partners to their applications, devices, and data, ensuring smooth and secure interactions across all touchpoints.
- Advanced Security with Adaptive Access: Protect critical resources and sensitive data by implementing strong authentication methods combined with risk-based adaptive access policies. These measures intelligently evaluate access scenarios, maintaining robust security without compromising user convenience or experience.
- Enhanced User Experience Across Multicloud Environments: Deliver seamless, fast, and reliable sign-in experiences, enabling users to remain productive while reducing reliance on password management. This unified approach not only enhances productivity but also minimizes IT support overhead.
- Centralized Identity Management: Simplify identity management by consolidating access to all applications—whether they are cloud-based or on-premises—into a single, unified platform. This centralized approach improves operational visibility and strengthens control over access and identities across the organization.
Who Benefits from Microsoft Entra ID?
Microsoft Entra ID serves as a versatile solution, offering tailored benefits to different roles within an organization:
- IT Administrators
- For IT administrators, Microsoft Entra ID provides robust tools to manage and secure access to applications and resources based on specific business needs. It enables administrators to implement policies such as multifactor authentication (MFA) for accessing critical organizational resources, enhancing security without compromising usability. IT admins can also automate user provisioning, seamlessly integrating Windows Server Active Directory (AD) with cloud-based applications, including Microsoft 365. Additionally, Microsoft Entra ID offers advanced identity protection and governance features, ensuring compliance and safeguarding user credentials.
- Application Developers
- App developers benefit from Microsoft Entra ID’s capabilities as a standards-based authentication provider. It simplifies the process of implementing single sign-on (SSO), allowing users to access applications using their existing credentials. Developers can also leverage Microsoft Entra APIs to build customized, data-driven applications that enhance user experiences by utilizing organizational data securely and efficiently.
- Microsoft 365, Office 365, Azure, and Dynamics CRM Online Subscribers
- Subscribers to Microsoft 365, Office 365, Azure, or Dynamics CRM Online are already utilizing Microsoft Entra ID, as each of these tenants is automatically a Microsoft Entra tenant. This integration enables organizations to immediately manage access to their connected cloud applications, streamlining operations and enhancing productivity.
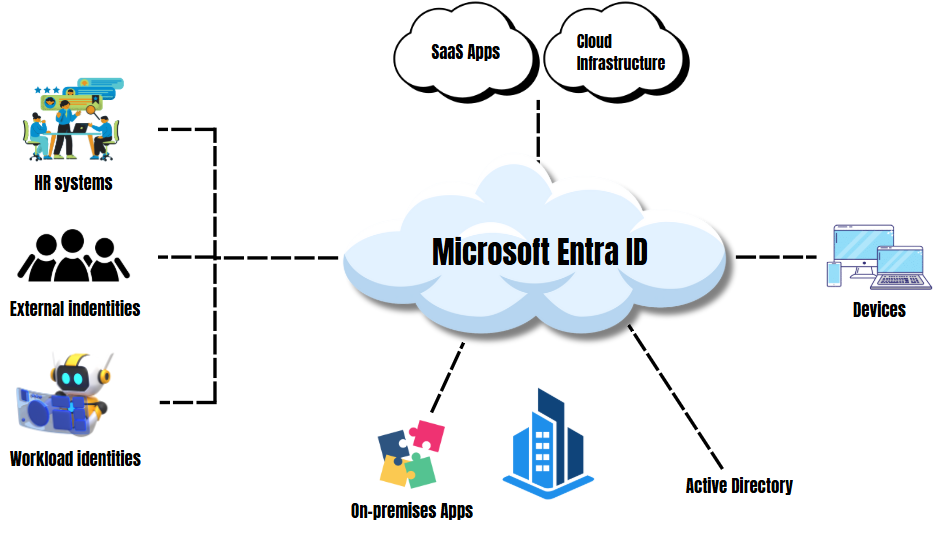
Features of Microsoft Entra ID
Microsoft Entra ID offers a robust suite of capabilities designed to secure and simplify identity and access management for modern organizations. With advanced features, Microsoft Entra ID empowers organizations to enhance productivity, streamline operations, and maintain strong security. The features are:
1. App Integrations and Single Sign-On (SSO)
Microsoft Entra ID streamlines application access by enabling seamless single sign-on (SSO) for your workforce. Regardless of location or device, the teams can securely connect to all their apps with a single set of credentials.
Key Benefits of SSO
- With SSO, users no longer need to remember multiple credentials or reuse passwords. A single set of credentials grants access to all applications, enhancing convenience and productivity.
- Minimize or eliminate repetitive sign-in prompts, providing a smooth, centralized app-launching experience that simplifies app discovery.
- By reducing the reuse of usernames and passwords across apps, SSO helps lower the risk of breaches.
- Manage user accounts efficiently by automatically granting or revoking app access based on group membership or role assignments.
Integration with Microsoft Entra App Gallery
The Microsoft Entra app gallery offers a catalog of thousands of pre-integrated cloud, SaaS, and on-premises applications, making it easy to deploy SSO and automated user provisioning. Popular apps like Workday, ServiceNow, Zoom, and Google Workspace are readily available, allowing quick and secure connections for your workforce.
Prebuilt Integrations for Productivity and Security
Microsoft Entra ID serves as a single identity system for both cloud and on-premises applications, simplifying management, improving control, and addressing critical security gaps. Prebuilt integrations enable rapid deployment of SSO and user provisioning, empowering teams to stay productive and secure:
- Connect apps like Cisco Webex, Slack, Workplace from Facebook, Adobe, Box, Dropbox Business, and DocuSign for real-time collaboration on shared documents.
- Automate employee onboarding and offboarding by integrating with HR systems such as SAP SuccessFactors and Workday.
- Provide more secure access to cloud and on-premises apps using solutions from Akamai, Cisco, F5, Palo Alto Networks, and other security providers.
2. Passwordless and Multifactor Authentication (MFA)
Microsoft Entra ID offers cutting-edge passwordless and multifactor authentication (MFA) solutions to safeguard access to applications and data while ensuring a seamless user experience. By eliminating reliance on passwords and employing advanced security methods, organizations can achieve stronger protection against breaches and credential theft.
- Stronger Security Beyond Passwords
- Passwords, even when complex, are vulnerable to identity attacks. Microsoft Entra ID enhances protection with MFA, requiring additional verification factors to strengthen defenses against lost or stolen credentials. These methods offer greater security than passwords alone, ensuring your organization remains resilient to evolving cyber threats.
- Protection Against Credential Theft
- High-risk accounts are often targeted by phishing and channel-jacking attacks. Microsoft Entra ID ensures credentials are resistant to these threats by leveraging secure authentication mechanisms, providing robust protection for sensitive accounts.
- Secure Access to Resources
- Before granting access to critical resources, Microsoft Entra ID verifies user identities to prevent unauthorized access. This approach ensures your organizational data and applications remain secure while supporting compliance with security policies.
- Seamless User Experience
- Microsoft Entra ID simplifies security processes to reduce friction for users. By offering user-friendly authentication methods, organizations can empower their workforce without compromising on security.
- Eliminating Password Risks
- Hackers often bypass security by exploiting weak or stolen passwords. With Microsoft’s passwordless authentication technology, one of the most common attack entry points is eliminated. This best-in-class technology transforms how users access their accounts, offering a more secure and convenient alternative.
- Industry Leadership in Standards
- As a founding member of the FIDO2 Alliance, Microsoft leads the way in advancing passwordless authentication standards. Organizations can take advantage of these innovations to adopt secure and compliant passwordless solutions.
- Reduced IT Overhead and Costs
- By going passwordless, organizations can reduce IT workload by eliminating the need for complex password policies and minimizing password reset support tickets. This allows IT teams to focus on more strategic tasks, improving overall efficiency.
- Convenient and Secure Options
- Microsoft Entra ID provides a range of secure and user-friendly options for passwordless authentication. Organizations can replace traditional passwords with methods such as biometric authentication, security keys, or other modern solutions that balance convenience and security.
3. Conditional Access
Microsoft Entra ID’s Conditional Access feature is a powerful policy engine designed to strengthen your organization’s security while maintaining productivity. By intelligently analyzing real-time signals, Conditional Access ensures the right level of access control is applied based on user behavior, device health, and contextual factors.
- Conditional Access uses a variety of real-time signals—such as user identity, device type, location, and session risk—to determine how users access corporate resources. Based on these signals, it can automatically allow, block, or limit access, or prompt for additional verification steps. This ensures security policies adapt dynamically without disrupting user workflows.
- It enables real-time monitoring and control over sessions and sensitive data within applications, whether they are on-premises or cloud-based. It analyzes user behavior within apps to detect unusual activities, applying restrictions or additional verification when necessary to safeguard organizational data.
- Conditional Access policies evaluate the health and security posture of registered devices. Only devices meeting specified security standards, such as compliance with patching requirements or endpoint protection configurations, are granted access to corporate resources. Devices that are vulnerable or compromised are automatically restricted to prevent unauthorized access.
- Microsoft Entra ID’s Conditional Access processes over 40 terabytes of identity-related security signals daily. These signals are analyzed using advanced machine learning algorithms to detect threats and apply the most appropriate access policies for each resource. This sophisticated approach ensures your organization stays ahead of potential risks while maintaining seamless user experiences.
4. Identity Protection
Microsoft Entra ID’s Identity Protection offers advanced capabilities to detect, remediate, and mitigate identity-based risks across your organization. By leveraging cutting-edge machine learning and adaptive security measures, Identity Protection ensures secure access while minimizing exposure to malicious activities.
- Microsoft Entra ID Protection uses advanced machine learning algorithms to monitor and analyze sign-in behaviors and user activities in real-time. It identifies risks such as unusual locations, anomalous device access, or suspicious behavior and automatically applies appropriate actions. Depending on the risk level, the system can block access, challenge users with additional authentication steps, limit permissions or allow access under certain conditions.
- It extends protection with risk-based adaptive access policies that dynamically adjust based on real-time signals. These policies help organizations respond quickly to threats, reducing the likelihood of credential compromise and unauthorized access by malicious actors.
- Microsoft Entra ID safeguards sensitive credentials with high-assurance authentication methods, such as multifactor authentication (MFA) or passwordless options. These advanced authentication techniques ensure that only legitimate users can access critical organizational resources, minimizing the risk of credential theft.
- Microsoft Entra ID Protection provides actionable intelligence that can be exported to Microsoft or third-party Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) tools. This integration allows security teams to conduct thorough investigations, enhance threat detection, and implement more robust security measures.
5. Strengthening Security with Privileged Identity Management (PIM)
Microsoft Entra ID’s Privileged Identity Management (PIM) enhances the security of your organization’s privileged accounts by limiting unnecessary or excessive access to critical resources. This solution helps safeguard sensitive operations by enforcing time-based, approval-based, and activity-monitored access to privileged roles.
PIM minimizes the risks associated with standing administrative privileges by implementing time-limited and approval-required access to critical roles. This ensures that admin accounts only have elevated access when absolutely necessary, significantly reducing the attack surface for malicious actors. Key Capabilities of Privileged Identity Management:
- PIM provides centralized tools to manage, monitor, and control access to vital organizational resources. By implementing the principle of least privilege, you can ensure that users only have the access they need, and nothing more.
- Privileged access is periodically reviewed, renewed, or revoked to maintain security. This process ensures that access rights remain aligned with organizational needs, reducing the risk of outdated or inappropriate permissions.
- Persistent administrative access is eliminated with PIM, as privileged roles are activated only for a specified duration. Once the time expires, access is automatically revoked, reducing the risk of unauthorized or accidental misuse.
- With Microsoft Entra PIM, organizations gain full visibility into privileged roles and accounts. You can identify who has access to what, track activation and usage of privileged roles, and receive real-time notifications when privileged accounts are activated, ensuring complete control and accountability.
6. End-User Self-Service
Microsoft Entra ID empowers employees to securely manage their own identity through intuitive self-service portals such as My Apps, My Access, My Account, and My Groups. This streamlined approach not only enhances the user experience but also strengthens security by giving employees greater control over their identity and access management. Microsoft Entra ID supports a range of self-service functionalities that streamline the user experience, including
- Password Reset: Employees can securely reset their passwords without requiring IT assistance, reducing downtime and IT support workloads.
- Account Management: Users have the ability to update personal details, reset passwords, and manage security settings directly, ensuring their accounts remain secure and up-to-date.
- App Launch and Discovery: Employees can easily access and discover applications from a centralized portal, improving productivity by simplifying app navigation.
- Sign-In Activity: Users can review their sign-in activity, increasing visibility and enhancing security by ensuring only authorized access to organizational resources.
- Access Lifecycle Management: Employees can request access, review permissions, and manage app access throughout the entire access lifecycle.
Furthermore, Microsoft Entra ID provides seamless integration with thousands of popular web-based apps, as well as custom cloud applications and legacy on-premises apps. This ensures a consistent and user-friendly self-service experience across all types of applications within the organization. Employees can register for both self-service password reset and multifactor authentication (MFA) in a single, unified process.
This integration ensures a smooth onboarding experience while enhancing security through additional authentication layer. By tracking usage patterns and analyzing interactions with self-service features, organizations can optimize the self-service portal and drive higher user adoption. These insights also enable the identification of potential security risks or areas where users may need additional training or support.
7. Unified Admin Center
The Unified Admin Center offers a centralized platform for managing all Microsoft Entra multicloud identity and network access solutions, providing administrators with a streamlined, comprehensive interface to control and oversee organizational security. This unified solution allows for efficient management of various identity and access management tasks across both cloud and on-premises environments, ensuring consistency and ease of administration. Whether it’s managing user access, enforcing security policies, or monitoring the overall health of your identity infrastructure, the Unified Admin Center brings all critical tools and resources into a single, intuitive interface.
Getting Started with Microsoft Entra ID
This section will guide you through the initial steps of setting up and configuring your Microsoft Entra ID environment.
– Creating a new tenant in Microsoft Entra ID
After signing in to the Azure portal, you can create a new tenant for your organization. This tenant represents your organization and allows you to manage a dedicated instance of Microsoft Cloud services for both internal and external users. Steps to Create a New Tenant:
- Sign In to the Azure Portal
- Begin by signing into your Azure portal account.
- Navigate to Microsoft Entra ID
- From the Azure portal menu, select Microsoft Entra ID to access the identity management settings.
- Manage Tenants
- Under Identity, go to Overview, then select Manage tenants to view your current tenants.
- Select Create
- Click on the Create button to initiate the tenant creation process.
- Choose Tenant Type
- On the Basics tab, choose the type of tenant you want to create:
- Microsoft Entra ID for standard identity management.
- Microsoft Entra ID (B2C) for business-to-consumer applications.
- On the Basics tab, choose the type of tenant you want to create:
- Proceed to Configuration
- Click Next: Configuration to proceed to the next step.
- Enter Configuration Details
- On the Configuration tab, input the following required details:
- Organization Name: Enter the name for your organization (e.g., “Contoso Organization”).
- Initial Domain Name: Enter a unique initial domain name (e.g., “Contosoorg”).
- Country/Region: Select your country or region from the dropdown menu, or leave the default United States option.
- On the Configuration tab, input the following required details:
- Review and Create
- After reviewing the entered information, click Next: Review + Create. Verify that all details are correct, and then select Create in the lower-left corner to complete the creation process.
Once the process is completed, your new tenant will be created with a default domain, such as contoso.onmicrosoft.com.
Your User Account in the New Tenant
Upon creating the new Microsoft Entra tenant, you automatically become the first user of that tenant. As the first user, you are granted the Global Administrator role, giving you full administrative privileges over the tenant.
To review your user account, navigate to the Users page in the portal. By default, you are listed as the technical contact for the tenant. This contact information can be modified in the Properties section.
Best Practices for Emergency Access
Microsoft recommends that organizations create two cloud-only emergency access accounts, both permanently assigned the Global Administrator role. These accounts should be used solely for emergency or “break glass” situations where normal administrative access is unavailable. These accounts should not be tied to specific individuals, and they should be protected following the emergency access account guidelines to ensure continuous administrative access if needed.
– Adding a Custom Domain Name to Your Microsoft Entra Tenant
By default, Microsoft Entra tenants are provisioned with an initial domain name, such as domainname.onmicrosoft.com. While this default domain cannot be changed or deleted, you can add your organization’s custom domain name (e.g., contoso.com) and set it as the primary domain. Adding a custom domain name allows you to use more familiar and user-friendly email addresses, such as [email protected], for your users.
Prerequisites:
Before you can add a custom domain name to your Microsoft Entra tenant, ensure that you have already registered the domain with a domain registrar.
Steps to Create Your Directory
Once you have registered your custom domain, you can create your directory in Microsoft Entra. Follow these steps:
- Sign in to the Azure Portal using an account with the Owner role for the subscription.
- Create Your Directory: Create a new tenant by following the steps outlined in the section titled Create a New Tenant for Your Organization.
Adding Your Custom Domain Name
After creating your directory, follow these steps to add your custom domain name to the tenant:
- Sign In to the Microsoft Entra Admin Center
- Sign in to the Microsoft Entra admin center with at least Domain Name Administrator privileges.
- Navigate to Domain Settings
- From the left-hand menu, go to Identity > Settings > Domain names.
- Add Custom Domain
- Select Add custom domain and enter your organization’s custom domain name (e.g., contoso.com) in the Custom domain name field. Then, click Add domain.
- The unverified domain will be added, and a page will appear displaying the DNS information required to validate your domain ownership. Save this information, as it will be needed for the verification process.
Adding DNS Information to Your Domain Registrar
To validate your custom domain, you need to add the DNS records provided in the previous step. Follow these instructions:
- Log In to Your Domain Registrar
- Access your domain registrar’s website and log in to your account.
- Create a DNS Record
- Create a new TXT or MX record using the DNS information you copied from the Microsoft Entra admin center. Set the Time to Live (TTL) for the record to 3600 seconds (1 hour) to ensure the changes take effect.
- Save the Record
- Save the new record in your domain registrar’s settings to initiate the verification process.
Verifying Your Custom Domain Name
Once the DNS record is added, it may take some time for the changes to propagate across the internet. Verification can be almost instantaneous or may take up to a few days, depending on your domain registrar.
To verify your custom domain name in Microsoft Entra, follow these steps:
- Sign In to the Microsoft Entra Admin Center
- Sign in as a Domain Name Administrator.
- Navigate to Domain Names
- In the admin center, go to Identity > Settings > Domain names.
- Select Your Custom Domain
- In the list of custom domain names, select the domain you added (e.g., contoso.com).
- Verify the Domain
- On the domain’s page, click Verify. This will confirm that your custom domain has been properly registered and is valid.
Once the verification process is complete, your custom domain name will be fully integrated into your Microsoft Entra tenant, and you can begin using it for your users’ email addresses and other identity management functions.
Best Practices for Microsoft Entra ID
Implementing and managing Microsoft Entra ID effectively requires a focus on security, performance, and governance. By adhering to best practices, organizations can maximize the benefits of this powerful IAM solution, minimize risks, and ensure a smooth and efficient user experience.
1. Security Best Practices
- Strong Authentication:
- Mandatory Multi-Factor Authentication (MFA): Enforce MFA for all users, including administrators, to significantly enhance account security. Utilize a variety of MFA methods such as authenticator apps, hardware tokens, and biometrics.
- Password Policies: Implement and enforce strong password policies, including minimum length, complexity requirements (uppercase, lowercase, numbers, symbols), and regular password rotations.
- Risk-Based Authentication: Leverage Conditional Access policies to dynamically adjust authentication requirements based on user risk levels (e.g., suspicious login attempts, device compromise).
- Least Privilege Principle:
- Minimize Permissions: Grant users only the minimum necessary permissions to perform their job functions.
- Regularly Review and Re-evaluate: Regularly review and re-evaluate user access rights and remove unnecessary permissions as needed.
- Security Audits and Monitoring:
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
- Monitoring and Alerting: Continuously monitor for suspicious activity, such as unusual login attempts, data exfiltration attempts, and account compromises. Configure alerts to notify security teams of critical events.
2. Performance and Scalability Best Practices
- Optimize Directory Synchronization:
- Efficient Filtering: Filter attributes during directory synchronization to minimize data transfer and improve performance.
- Schedule Synchronization: Schedule synchronization windows to avoid peak usage times and minimize impact on network resources.
- Monitor Synchronization Errors: Regularly monitor for and resolve synchronization errors to ensure data accuracy and consistency.
- Capacity Planning:
- Monitor Usage: Monitor user activity, authentication volumes, and other key performance indicators to assess current and future capacity needs.
- Plan for Growth: Scale resources as needed to accommodate increasing user demands and ensure consistent performance.
3. Governance and Compliance Best Practices
- Access Governance:
- Implement Role-Based Access Control (RBAC): Define and enforce clear roles and responsibilities for user access.
- Utilize Privileged Identity Management (PIM): Implement PIM to control and monitor administrative privileges, such as granting just-in-time access and enforcing time-bound permissions.
- Compliance Requirements:
- Meet Industry Standards: Ensure compliance with relevant industry standards and regulations (e.g., GDPR, HIPAA, SOC 2) through effective access controls and data protection measures.
- Maintain Audit Logs: Maintain detailed audit logs of all user activities, including login attempts, access requests, and administrative actions.
Conclusion
Microsoft Entra ID plays a vital role in today’s evolving security landscape. By effectively implementing and managing this powerful cloud-based identity and access management service, organizations can significantly enhance their security posture, improve employee productivity, and streamline IT operations. By adhering to best practices for security, performance, and governance, organizations can maximize the return on their Entra ID investment while ensuring compliance with industry regulations. We encourage you to explore the features and capabilities of Microsoft Entra ID further and embark on your journey towards a more secure and efficient digital future.


