The Ethical Hacking Certification – CEH (312-50) is for people who want to become certified as ethical hackers. It’s provided by the International Council of E-Commerce Consultants (EC-Council), a worldwide authority in information security certification.
The CEH certification is designed to validate the skills and knowledge of individuals who want to become ethical hackers or security professionals. The exam covers a wide range of topics related to ethical hacking, including network scanning, vulnerability analysis, system hacking, web application hacking, and social engineering.
Ethical Hacking Certification-CEH -312 -50 Exam Glossary
Here are some terms that you may come across when studying for the Ethical Hacking Certification – CEH (312-50) exam:
- Ethical Hacking: The process of testing and evaluating computer systems or networks to find security vulnerabilities that could be exploited by malicious attackers.
- Vulnerability: A vulnerability in a computer system or network is like a weakness that attackers can use to get in without permission or to cause harm.
- Exploit: A program or code that uses a weakness to get into a computer system or network without permission and do things it’s not supposed to do.
- Penetration Testing: Checking a computer system or network to find security problems and see how well the current security measures work.
- Footprinting: The process of gathering information about a target system or network through passive or active reconnaissance techniques.
- Scanning: The process of identifying open ports, services, and vulnerabilities on a target system or network using automated tools or manual techniques.
- Social Engineering: The use of deception or manipulation to trick individuals into divulging sensitive information or performing actions that could compromise the security of a system or network.
- Malware: Malicious software that is designed to perform unauthorized actions on a computer system or network, such as stealing data, encrypting files, or disrupting operations.
- Encryption: The process of changing regular text into secret code using a special method to keep important information private.
- Firewall: A device that keeps an eye on and manages the data going in and out of a network according to established security rules.
- Intrusion Detection System (IDS): A safety system that watches the data moving in a network for any hints of unusual or harmful actions and tells the people in charge if it finds anything that might be a threat.
- Incident Response: When something bad happens like a cyberattack or data breach, dealing with it to make the damage as small as possible and make sure it doesn’t happen again is called incident response.
Ethical Hacking Certification-CEH -312 -50 Study Guide
Here are some official resources and links to help you prepare for the Ethical Hacking Certification – CEH (312-50) exam:
- EC-Council’s CEH Certification page: https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/ This is the official certification page for the CEH exam on the EC-Council website. It provides information on the certification requirements, exam objectives, and registration process.
- CEH Exam Blueprint: https://www.eccouncil.org/wp-content/uploads/2020/06/CEH-Exam-Blueprint-v3.0.pdf This is the official exam blueprint for the CEH (312-50) exam. It outlines the exam objectives and the percentage of questions that will be asked on each topic.
- CEH Exam Study Guide: https://www.eccouncil.org/wp-content/uploads/2021/03/CEHv11-Study-Guide.pdf This is the official study guide for the CEH (312-50) exam. It provides detailed information on the exam objectives, as well as study tips and practice questions.
- CEH Exam Prep App: https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/ceh-exam-prep-app/ This is the official CEH exam prep app from EC-Council. It provides practice questions, flashcards, and a timer to simulate the exam experience.
- CEH Online Lab: https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/ceh-online-lab/ This is an online lab environment designed to help you practice your ethical hacking skills in a safe and controlled environment.
Ethical Hacking Certification-CEH -312 -50 Exam Tips and Tricks
Here are some tips and tricks to help you prepare for and pass the Ethical Hacking Certification – CEH (312-50) exam:
- Understand the exam objectives: The CEH exam blueprint provides a breakdown of the exam objectives and the percentage of questions that will be asked on each topic. Make sure you understand the exam objectives and focus your study efforts accordingly.
- Use multiple study materials: To make sure you really understand what you need to for the exam, use different study tools like books, online courses, practice tests, and study guides.
- Practice, practice, practice: Take practice tests and quizzes to figure out what you’re good at and where you need to study more. This way, you can concentrate on the areas that need improvement.
- Stay up-to-date with industry developments: Stay updated on the newest things happening in the industry, like new weaknesses, ways to exploit them, and security tools. This helps you stay current and have a good overall knowledge of the field.
- Understand the tools and techniques: Understand the different types of hacking tools and techniques used by attackers and ethical hackers to identify vulnerabilities and exploit them.
- Read the questions carefully: Read the exam questions carefully and make sure you understand what is being asked before selecting your answer. Don’t rush through the questions, and take your time to analyze the scenario and the options available.
- Manage your time wisely: The CEH exam is timed, so make sure you manage your time wisely and don’t spend too much time on a single question. If you are unsure of an answer, move on to the next question and come back to it later if you have time.
- Take breaks: Take breaks during your study sessions and on the day of the exam to avoid burnout and ensure that you are focused and alert.
- Get hands-on experience: Gain hands-on experience by practicing ethical hacking techniques in a safe and legal environment, such as a virtual lab or a sandbox environment.
- Stay calm and confident: On the day of the exam, stay relaxed and self-assured, and have confidence in what you’ve learned and prepared for. Remember to take deep breaths and don’t let anxiety or nervousness get in the way of how well you do.
Course Outline
The important topics of the exam includes:
- Introduction to Ethical Hacking
- Footprinting and Reconnaissance
- Scanning
- Networks Enumeration
- System Hacking
- Malware Threats
- Sniffing
- Social Engineering
- Denial of Service
- Session Hijacking
- Hacking Web servers
- Hacking Web Applications
- SQL Injection
- Hacking Wireless Networks
- Hacking Mobile Platforms
- Evading IDS, Firewalls, and Honeypot
- Cloud Computing
- Cryptography
CEH Certified Ethical Hacker Study Guide
The Certified Ethical Hacker (CEH) accreditation is a well-respected and well-trusted ethical hacking certification in the industry. Furthermore, this will add value to your resume and help you advance in your job. Due to increased demand, Certified Ethical Hackers now work with some of the best and largest corporations in fields including as healthcare, finance, government, and energy. So, if you’ve decided to pursue this qualification, you’ll need to back it up with hard work. We’ll go through the tactics and approaches that will help you prepare for the test in the sections below.
1. Create a Study time table
Yes, the best way to start preparing for the exam is to first set the time table. That is to say, try to create study hours accordingly in which you only study. As for becoming a hacker you need to have a hacker mindset, so you need more extra time to understand the concepts. By doing so you can easily maintain your study flow while ignoring the distractions.
2. Understanding Ethical Hacking Domains
To get advanced, you have to get into the core of this certification exam. That is to say, you need to have a high understanding in hacking and as well as the other systematic process. This exam is going to test your knowledge on the basis of the domains they provide. If you master the domains then it will help you a lot to pass the exam. The Certified Ethical Hacker (CEH) syllabus covers the following domains:
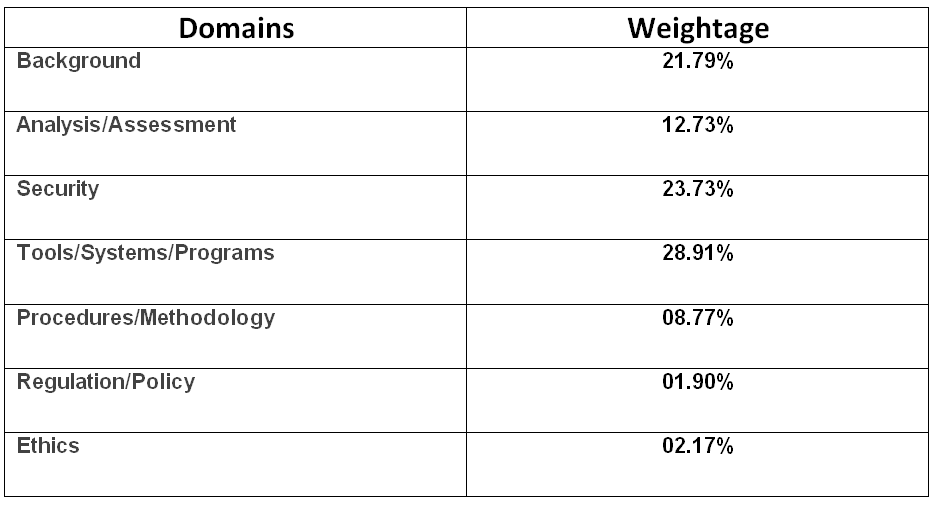
Background
This include sub-domains:
- Firstly, Network and Communication Technologies
- Secondly, Information Security Threats and Attack Vectors
- Then, Information Security Technologies
Analysis / Assessment
The sub-domains in this are:
- Firstly, Information Security Assessment and Analysis
- Then, Information Security Assessment Process
Security
It includes:
- Information Security Controls
- Then, Information Security Attack Detection
- Lastly, Information Security Attack Prevention
Tools / Systems / Programs
Sub-domains in this are:
- Firstly, Information Security Systems
- Then, Information Security Programs
- Information Security Tools
Procedures / Methodology
This include:
- Information Security Procedures
- After that, Information Security Assessment Methodologies
Regulation / Policy
It include sub-domain that is:
- Information Security Policies/ Laws/Acts
Ethics
This includes:
- Ethics of Information Security
Use the step by step CEH Certified Ethical Hacker Study Guide for better preparation!
3. Online Training Program
The training programs will help you to become professionally certified as an Ethical Hacker. However, these programs will provide you advanced knowledge of hacking tools and techniques. In this, you will work on your own system by scanning, testing, hacking, and securing it. This Certified Ethical Hacker (CEH) training course will help you in learning the different approaches based on five phases. This includes enumeration, maintaining access, covering your tracks, reconnaissance, and gaining access.

Moreover, the main thing is to be passionate about your goal. To become an ethical hacker it is necessary that you should think and perform like a hacker.
4. Join Online Study Groups
Joining online study groups and communities is a great way to explore what is happening in the world of hacking. As there are big communities of hackers spread across globally. In these groups you get access to get in touch with both beginners and professionals. Moreover, here you can comfortably share your issue or problem related to the hacking.
5. Practice Exams
Certified Ethical Hacker (CEH) practice exams play an important role during your preparation. These tests will help you to know about the weak and strong areas. For that, you need to take these exams as the real exam to understand things better. In this even if you scoreless for the first time but you get to know where you were wrong and vice versa. However, there are many training providers out there that offer free Certified Ethical Hacker (CEH) practice exam tests for the Certified Ethical Hackers exam.
What’s next? After becoming Certified Ethical Hacker, what skills and abilities do we get. Moreover, what is the market value of ethical hackers?
Ethical Hackers: Market Value
Ethical hacker is an expert that helps companies to realize their vulnerabilities. They basically work for businesses or government organizations. However, from the past year the threat over cloud computing has increased, This has created a fear amongst top organizations for their data. As a result, the demand for ethical hackers is showing good growth because every other company needs to protect their data. The ethical hackers have proficient knowledge of various operating systems and hacking techniques.
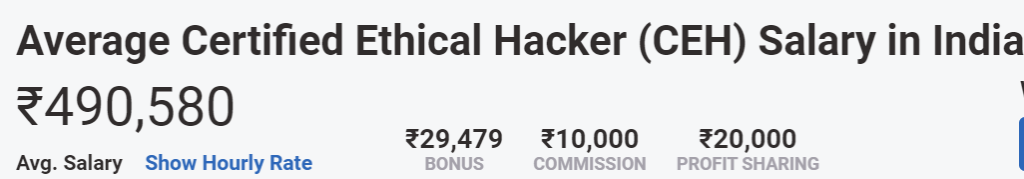
Salary of Ethical Hacker
What you will learn as an Ethical Hacker
- Firstly, you will know about various types of footprinting, footprinting tools, and countermeasures.
- Secondly, you will learn about network scanning techniques and scanning countermeasures.
- Thirdly, working on system hacking methodology, steganography, steganalysis attacks, and covering tracks.
- Then, you will learn about different types of Trojans, Trojan analysis, and Trojan countermeasures.
- Moreover, you will get working knowledge of viruses, virus analysis, computer worms, malware and countermeasures.
- Lastly, you will learn about various types of penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. In addition, you will get to know about different threats to IoT platforms and learn how to defend IoT devices securely.
Final words
In our world today, terrorist groups are giving money to cybercriminals to break into security systems and cause various digital threats. This has made cybercrime more common. Deciding to become an Ethical Hacker is a good choice now, but it won’t be simple. Many companies struggle to keep their systems safe from hackers and need experts to help. So, there’s a big demand for skilled Ethical Hackers, but you must become really good at it. That is to say, there is a lot to practice and to work so that you get certified as a professional ethical hacker. Lastly, prepare well and crack the exam with a good score. Stay safe!
Upgrade your ethical hacking skills. Become a Certified Ethical Hacker Now!


