Every year, there are so many candidates who apply for Administration of Symantec Endpoint Detection And Response (4.2):251/250-555 Exam. But, have you ever wondered, how many of them actually qualify this certification exam? It’s not that the exam is difficult. Rather, the problem lies in their preparation. Therefore, in this article, we’re going to provide you with a comprehensive study guide for the same. But before you fasten your seat belts and get all pumped to prepare for the exam, we say hold your horses for a while.
Before understanding all the learning resources, it’s important you first get acquainted with all the exam details. Since this process will lead you to a better start. And, you know what they say, a better start always lead to a great end. In the same light, let’s begin with Exam overview.
Familiarize with Exam Information
It’s not always the hard work that leads to your success, but the smart work, when it comes to the certification exam. So, for your convenience, we have laid every exam detail that you must know beforehand.
Exam Overview
With 251/250-555 Exam, candidates can certify technical knowledge and competency by becoming a Symantec Certified Specialist (SCS) based on your specific area of Symantec technology expertise. In order to achieve this certification, candidates must qualify for the proctored SCS exam. As this exam is based on a combination of Symantec training material, commonly referenced product documentation, and real-world job scenarios.
This exam is intended for the IT Professionals practising the Symantec Endpoint Detection and Response (SEDR) product in a Security Operations role. This certification exam examines the candidate’s acquaintance on how to detect, investigate, remediate, and recover from an incident using Symantec Endpoint Detection and Response in their organizations.
Qualifying the certification exam, the certified candidate will be able to the following tasks-
- Firstly, he/she will be able to demonstrate an understanding of the planning,
- Secondly, the candidate will also be able to design, deploy and optimize Symantec Endpoint Detection and Response.
All this understanding serves as a foundation of technical knowledge and competency for the Symantec Endpoint Detection and Response solution in an enterprise environment. Therefore, to achieve this level of certification, candidates must pass the technical exam and accept the Certification Agreement.
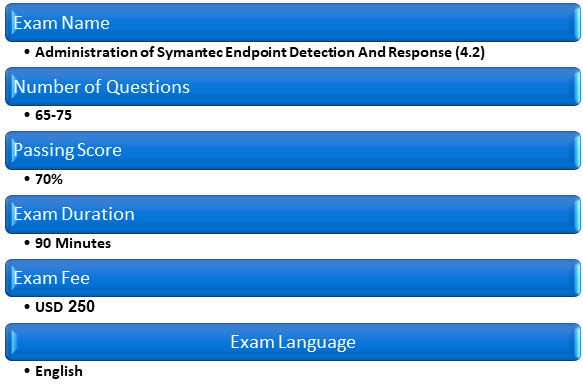
Basic Exam Details
As for the basic exam details, you need to just keep in mind that the exam comprises of around 65-75 questions. And, the candidate will be given only 90 minutes to complete the 251/250-555 Exam. As for the qualifying bar, candidates must score 70% and above. However, the exam is only available in the English language. In addition to it, the exam registration fee is USD 250. But one must check according to their own region since the price varies from country to country.
Recommended Experience
It is recommended for a candidate to have at least 3-6 months experience with Symantec EDR solutions. Further, they must have the ability to complete the following-
- Firstly, operational knowledge of Symantec Endpoint Detection and Response.
- Secondly, familiarity with Cybersecurity and Threat Protection concepts.
- Subsequently, familiarity with Symantec Endpoint Protection products.
- Also, perform Symantec EDR planning steps.
- In addition, perform Symantec EDR implementation steps.
- Further, perform initial Symantec EDR configuration steps.
- Not to mention, perform basic Symantec EDR administration actions.
- Moreover, configure Symantec EDR to integrate and share data with other applications.
- Consequently, able to investigate threats in the environment.
- Furthermore, able to act on threats in the environment.
- Additionally, able to recover after threats have been contained.
- Last but not least, able to report on threats in the environment.
Exam Objectives
The exam objectives are the most important aspect of any certification exam. So, make sure to follow the below list.
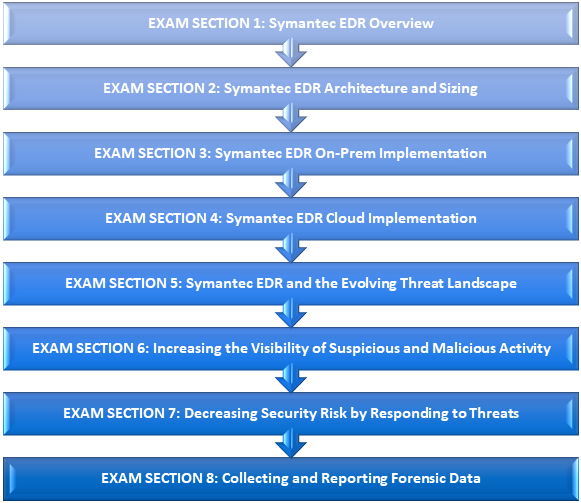
EXAM SECTION 1: Symantec EDR Overview
- Firstly, describing the Symantec EDR Shared Technologies.
- Secondly, describing the Symantec EDR product add-ons.
EXAM SECTION 2: Symantec EDR Architecture and Sizing
- Firstly, describing the Symantec EDR Architecture
- Subsequently, describing sizing a Symantec EDR implementation.
EXAM SECTION 3: Symantec EDR On-Prem Implementation
- First of all, describing the Symantec EDR System Requirements.
- Secondly, describing the Symantec EDR Bootstrapping process
- Subsequently, describing the Symantec EDR Initial Configuration process.
- Also, describing Symantec EDR User-Managed Certificates.
- In addition, describing the Symantec EDR On-Prem User Accounts and Roles
- Lastly, describing the process of integration Symantec EDR with Symantec Endpoint Protection
EXAM SECTION 4: Symantec EDR Cloud Implementation
- First thing first, describing the Symantec EDR Cloud User Accounts and Roles.
- Also, describing Symantec EDR Cloud Network Ranges
- Not to mention, describing Symantec EDR Cloud Dissolvable Agent Servers
- Furthermore, describing Symantec EDR Cloud Dissolvable Agent Server Configurations
- Lastly, describing Symantec EDR Cloud Collection Service Agents
EXAM SECTION 5: Symantec EDR and the Evolving Threat Landscape
- First of all, describing the capabilities and functions of Symantec EDR
- Subsequently, describing the challenges faced when threat hunting in the environment and their resultant business objectives.
- Also, describing how Symantec EDR meets business objectives
EXAM SECTION 6: Increasing the Visibility of Suspicious and Malicious Activity
- First thing first, describing the benefits and outcomes of increasing the visibility of suspicious and malicious activity in the environment
- Secondly, describing how SEDR increases the visibility of suspicious and malicious activity in a typical environment
- Thirdly, describing the various types of suspicious and malicious activity found in a typical environment.
- Subsequently, describing installation prerequisites, minimum solution configuration and installation procedures required to identify threats.
- Also, describing the methods used to identify evidence of suspicious and malicious activity
- Not to mention, describing the methods used to enable automated security incident notifications with SEDR
- In addition, describing the various types of Indicators of Compromise (IoC) found in a typical environment.
- Furthermore, describing installation prerequisites, minimum solution configuration and installation procedures required before identifying IOCs.
- Lastly, describing the methods used to search for IOCs using SEDR.
EXAM SECTION 7: Decreasing Security Risk by Responding to Threats
- First thing first, describing the benefits of reducing security risks by responding to threats in the environment.
- Secondly, describing the methods SEDR uses to respond to threats in a typical environment
- Subsequently, describing the various methods used to isolate threats in a typical environment.
- Not to mention, describing installation prerequisites, minimum solution configuration and installation procedures required to isolate threats.
- Further, determining the appropriate method for isolating threats to reduce security risk
- Also, describing the various methods used to block threats in a typical environment.
- Additionally, describing installation prerequisites, minimum solution configuration and installation procedures required to block threats.
- Likewise, determining the appropriate method for blocking threats to reduce security risk.
- Furthermore, describing the various methods used to remove threats in a typical environment.
- Moreover, describing installation prerequisites, minimum solution configuration and installation procedures required to remove threats.
- Last but not least, determining the appropriate method for removing threats to reduce security risk.
EXAM SECTION 8: Collecting and Reporting Forensic Data
- First of all, describing the benefits of collecting and reviewing forensic information.
- Secondly, describing how SEDR can be used to collect and review forensic information for further investigation of security incidents.
- After this, describing the various forms of information collected by SEDR in a typical environment
- Additionally, describing installation prerequisites, minimum solution configuration and installation procedures required to collect forensic data
- Further, determining the appropriate method for the collection of forensic data using SEDR
- Moreover, describing the methods used to create post-incident reports and the benefits to forensic analysis it provides.
- Lastly, determining the appropriate method to create a post-incident report using SEDR.
Finally, this is an end to this long list of exam objectives. Although, on the first impression, it may look as difficult to prepare. But not to fret. In the subsequent section, we are providing you will all the relevant learning resources. Since all the learning resources will help you with completing each and every exam objective. So, without second-guessing yourself, let’s move on to the next section.
Exam Study Guide: 251/250-555 Exam
This is no ordinary exam guide, here we are providing you with each and every learning resources so that this 251/250-555 Exam doesn’t feel like a burden. So, let’s begin with our first step in the guide.

Understand and Review Objectives
While preparing for the certification exam, one must first go through all the exam objectives and details. This implies, to first review all the exam objectives, before sitting for the exam. Therefore, make sure to go through the following details-
- Firstly, make sure you have the recommended experience of at least 3-6 months with Symantec EDR solutions
- Secondly, the candidate must have an understanding of the operational knowledge of Symantec Endpoint Detection and Response.
- Secondly, he/she must be familiar with Cybersecurity and Threat Protection concepts.
- Subsequently, familiarity with Symantec Endpoint Protection products.
- Also, they must be able to perform Symantec EDR planning steps.
- In addition, the candidate should know how to perform Symantec EDR implementation steps.
- Further, the must be able to perform initial Symantec EDR configuration steps.
- Additionally, they should have the basic understanding fo performing basic Symantec EDR administration actions.
- Moreover, knowledge about the configuring Symantec EDR to integrate and share data with other applications.
- Furthermore, he/she should be able to investigate threats in the environment.
- Of course, the ability to act on threats in the environment.
- By the same token, the ability to recover after threats have been contained.
- Last but not least, the ability to report on threats in the environment.
Instructor-led Training- the Gold standard
After reviewing the exam details, it’s time for you to go through the instructor-led training. Instructor-led training is the gold standard when it comes to certification exams. So, you have two options to choose from here. You can either go for one of them or both, It’s totally up to you.
Symantec Endpoint Detection and Response 4.2 Planning and Implementation (2 Day Classroom/Virtual)
Symantec EDR Overview
- Introduction to Symantec Endpoint Detection and Response (Lecture)
- Shared Technologies (Lecture)
- Product Add-Ons (Lecture)
- Product Integrations (Lecture)
- Symantec EDR Architecture and Sizing
- On one hand, Symantec Endpoint Detection and Response Architecture (Lecture/Lab)
- On the other hand, Symantec Endpoint Detection and Response Sizing (Lecture/Lab)
- Symantec EDR On-Prem Implementation
- System Requirements (Lecture)
- Bootstrapping (Lecture/Lab)
- Initial Configuration (Lecture/Lab)
- Symantec Endpoint Detection and Response On-Prem Console Overview (Lecture)
- Managing Certificates (Lecture/Lab)
- User Accounts and Roles (Lecture/Lab)
- Lastly, Symantec Endpoint Protection Integration (Lecture/Lab)
- Symantec EDR Cloud Implementation
- To begin with, Symantec EDR Cloud Console Overview (Lecture)
- User Accounts and Roles (Lecture)
- Network Ranges (Lecture/Lab)
- Dissolvable Agent Configurations (Lecture/Lab)
- Dissolvable Agent Servers (Lecture/Lab)
- Collection Service Agents (Lecture/Lab)
Symantec Endpoint Detection and Response 4.2 Administration (2 Day Classroom/Virtual)
- Introduction to Symantec EDR
- Challenges of Threat Hunting with Endpoint Detection (EDR) in the environment
- How Symantec Endpoint Detection and Response meets User Stories
- Increasing the Visibility of Suspicious and Malicious Activity
- Identifying Evidence of Suspicious & Malicious Activity (Lecture/Lab)
- Searching for Indicators of Compromise (Lecture/Lab)
- Decreasing Security Risk by Responding to Security Threats
- Isolating Threats in The Environment (Lecture/Lab)
- Blocking Threats in The Environment (Lecture/Lab)
- Removing Threats in The Environment (Lecture/Lab)
- Collecting and Analyzing Forensic Data for the Investigation of Security Incidents
- Collecting Forensic Information (Lecture/Lab)
- Analyzing Forensic Information (Lecture/Lab)
Cut the pressure with E-learning
E-learning is a new way of studying that has been widely accepted globally. It allows the candidate to gain knowledge from sitting in any part of the world. It cuts down the pressure and helps the learner understand their objectives more clearly. So, make sure to go through the E-learning classes. Symantec provides you with this particular module. So, let’s check out the course.
Symantec EDR 4.2 Administration eLearning
- First of all, introduction to Symantec EDR
- Secondly, increasing the Visibility of Suspicious and Malicious Activity
- Also, decreasing Security Risk by Responding to Security Threats
- Lastly, collecting and Analyzing Forensic Data for the Investigation of Security Incidents
Go through the Documentation
Documentation, as the name suggests, is the official information, So, here are the official study guides, you must try and give it a read.
- To begin with, Symantec EDR 4.2 Sizing and Scalability Guide
- Subsequently, Symantec EDR 4.2 Installation Guide for Dell 8840 and 8880 Appliances Symantec EDR 4.2 Installation Guide for Virtual Appliances
- Not to mention, Symantec EDR 4.1 Security Operations Guide
- In addition, Symantec Threat Discovery Guide
- Lastly, Symantec EDR 4.1 Search Fields Reference
Join an Online Community
Online forums and study groups are a great way to prepare for the 251/250-555 Exam. Therefore, feel free to get in touch with other candidates through study forums or online groups to ask a question related to the topic you’re having difficulty with.
However, it’s not something you have to join. It’s just something very subjective. Not to mention, these online groups help you stay equated with the other people who are also walking through the same path as yours. Moreover, you can also ask a question related to the topic you’re having difficulty with.
Practice Sets for 251/250-555 Exam
And, finally, it’s time for practice sessions. Take it from us, Self Evaluation is the only step you need in the end. The more you’re going to practice, it’s better for you.
Not only does it helps you understand the areas where you lack but also, ensure you’re strengthening your skills as well. So, go through as many practice tests as much you can. FOR MORE PRACTICE TEST, CLICK HERE!
And, this marks the end to the preparatory guide. In the end, we would just like to remind you that, your effort never gets wasted. And, if you aspire to take your career to the next level, it’s time you get certified. Therefore, make sure to follow the preparatory guide mentioned above and we’re sure you will succeed.


