Google Professional Cloud Security Engineer is responsible for designing and implementing a secure infrastructure on the Google Cloud Platform. For this, they have an understanding of security best practices and industry security requirements. They design, develop and manage a secure infrastructure leveraging Google security technologies.
The cheat sheet for Google Professional Cloud Security Engineer (GCP) will provide you with a brief overview of all the materials you’ll need to pass the test. It will also be a treasure of knowledge for you. This cheat sheet will make last-minute modifications a breeze because it contains all of the necessary resources as well as the best revision technique. But, before we get started on your revision, let’s have a look at the test specifics.
Google Professional Cloud Security Engineer Exam Glossary
Here are some key terms and concepts you should be familiar with when preparing for the Google Professional Cloud Security Engineer exam:
- Identity and Access Management (IAM): A GCP service that allows you to manage access to cloud resources by creating and managing IAM roles and permissions.
- Virtual Private Cloud (VPC): A private, isolated virtual network within GCP that you can configure and manage.
- Firewall Rules: Security rules that control inbound and outbound network traffic to and from your GCP resources.
- Security Groups: A way to group related GCP resources together and apply firewall rules to those resources.
- Cloud Load Balancing: A service that distributes incoming traffic across multiple backend instances to increase availability and reduce latency.
- Cloud CDN: A content delivery network service that caches and delivers content from Google’s global network of edge locations.
- Encryption: The process of converting data into a code to prevent unauthorized access.
- Cloud Key Management Service (KMS): A GCP service that allows you to manage cryptographic keys and encrypt data.
- Data Classification: A process of categorizing data based on its sensitivity or criticality.
- Compliance: The procedure of complying with regulations and industry standards like GDPR, HIPAA, and PCI DSS.
- Incident Response: The process of identifying, analyzing, and responding to security incidents in a timely manner.
- Post-Incident Review: The process of examining and evaluating a security incident post-occurrence to pinpoint areas for enhancement and forestall future incidents.
- Cloud Security Command Center: A GCP service that provides a centralized view of your cloud assets, vulnerabilities, and security threats.
- Learn Cloud Armor: A service that provides security policies and protection against DDoS attacks and other threats.
- Cloud DLP: A data loss prevention service that helps you discover, classify, and protect sensitive data in GCP.
Google Professional Cloud Security Engineer Exam Guide
Here are some official resources from Google that you can use to prepare for the Professional Cloud Security Engineer exam:
- Exam Guide: The official exam guide provides an overview of the exam format, recommended experience and skills, and a detailed list of topics that will be covered on the exam. You can find the exam guide here: https://cloud.google.com/certification/cloud-security-engineer
- Training Courses: Google offers a variety of training courses and learning paths to help you prepare for the exam. Some of the recommended courses include:
- Security Best Practices in Google Cloud: This course covers best practices for securing your GCP resources and managing identity and access. You can find the course here: https://cloud.google.com/training/course/security-best-practices-in-google-cloud-platform
- Google Cloud Security Essentials: This course provides an introduction to GCP security concepts and features. You can find the course here: https://cloud.google.com/training/course/google-cloud-security-essentials
- Security in Google Cloud Platform: This advanced course covers topics such as network security, data protection, and incident management. You can find the course here: https://cloud.google.com/training/course/security-in-google-cloud-platform
- Practice Exam:
- Google provides a practice exam that mimics the format and level of difficulty encountered in the real exam. Utilizing this practice test can assist you in pinpointing the areas that require concentrated study. You can find the practice exam here: https://cloud.google.com/certification/practice-exam/cloud-security-engineer
- Documentation: Google’s documentation provides detailed information on all of the GCP services and features related to security. Reviewing the documentation can help you understand how to configure and use these services effectively. You can find the documentation here: https://cloud.google.com/security
- Community: Google has an active community of cloud professionals who share their experiences and insights on topics related to GCP security. Becoming part of the community can facilitate your learning from peers and keeping yourself current with the most recent trends and best practices. You can find the community here: https://cloud.google.com/community/security
Expert tips to pass the Google Professional Cloud Security Engineer Exam
Here are some suggestions on how to get ready for the Google Professional Cloud Security Engineer test:
- Examine the exam guide: The official exam guide contains a detailed list of subjects that will be covered on the test. It is critical to review the guide meticulously and focus your attention on the areas where you require the most improvement.
- Gain practical experience: GCP provides a free tier that allows you to experiment with GCP services and functions. Develop a test environment and practice securing and configuring GCP resources. This will assist you in gaining practical experience and applying the principles you study.
- Take the practice exam: Google provides a practice exam that mimics the format and complexity level of the actual exam. Taking the practice exam can assist you in identifying areas where you need to concentrate your studying and becoming familiar with the sorts of questions that will be on the exam.
- Concentrate on significant subjects: Network security, data protection, compliance and auditing, and incident management are some of the major topics covered on the exam. It is essential to review these topics thoroughly and understand how to configure and utilize the related GCP services and features.
- Utilize official resources: Google provides a variety of official resources, including training courses, documentation, and a community of cloud professionals, to help you prepare for the exam. Make sure to use these resources to supplement your studies and gain insights from others who have taken the exam.
- Manage your time effectively: The exam is timed, so it is important to manage your time effectively. Don’t spend too much time on any one question, and make sure to review your answers before submitting the exam.
Skills validation:
The Professional Cloud Security Engineer exam assesses the candidate’s ability in –
- Firstly, Configuring access within a cloud solution environment
- Secondly, Configuring network security
- Thirdly, Ensuring data protection
- Also, Managing operations within a cloud solution environment
- Finally, Ensuring compliance
Cheat Sheet: Google Professional Cloud Security Engineer
This Cheat Sheet will help you plan the right strategy to pass the exam and attain your desired certification, and hence gain high-paying career options. Follow the Steps and reach new heights in your career!
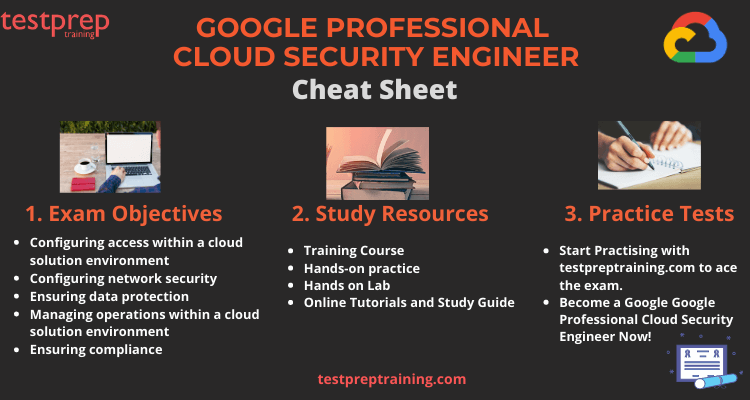
1. Understand the Exam Objectives
The first step in your Cheat Sheet is to visit the Google Professional Cloud Security Engineer Official Website. This will unquestionably put you on the right track. Remember, the official website is the most trusted website. Next, it’s time to hit the exam guide. The course domains act as a blueprint for the exam. You should be very clear with the syllabus of exam. Have utmost clarity about the exam course and concepts to score better in the exam. This Google Professional Cloud Security Engineer Course covers the following domains:
Topic 1: Configuring access (27%)
1.1 Managing Cloud Identity. Considerations include:
- Configuring Google Cloud Directory Sync and third-party connectors (Google Documentation: Set up Integration Connectors)
- Management of super administrator account (Google Documentation: Super administrator account best practices, Creating and managing organizations)
- Automating the user lifecycle management process (Google Documentation: Object Lifecycle Management)
- Administering user accounts and groups programmatically (Google Documentation: Managing users programmatically)
- Configuring Workforce Identity Federation (Google Documentation: Configure Workforce Identity Federation)
1.2 Managing service accounts. Considerations include:
- Securing and protecting service accounts (including default service accounts) (Google Documentation: Best practices for using service accounts)
- Identification of scenarios requiring service accounts (Google Documentation: Understanding service accounts, Service accounts)
- Creating, disabling, and authorizing service accounts (Google Documentation: Disable and enable service accounts)
- Securing, auditing and mitigating the usage of service account keys (Google Documentation: Best practices for managing service account keys)
- Managing and creating short-lived credentials (Google Documentation: Create short-lived credentials for a service account)
- Configuring Workload Identity Federation (Google Documentation: Configure Workload Identity Federation with AWS or Azure)
- Managing service account impersonation (Google Documentation: Service account impersonation)
1.3 Managing authentication.
- Creating a password and session management policy for user accounts
- Setting up Security Assertion Markup Language (SAML) and OAuth (Google Documentation: Signing in users with SAML)
- Configuring and enforcing two-step authentication (Google Documentation: Multi-factor authentication (MFA))
1.4 Managing and implementing authorization controls. Considerations include:
- Managing privileged roles and separation of duties with Identity and Access Management (IAM) roles and permissions (Google Documentation: Separation of duties and Identity and Access Management roles)
- Managing IAM and access control list (ACL) permissions (Google Documentation: Access control lists (ACLs))
- Granting permissions to different types of identities, including using IAM conditions and IAM deny policies (Google Documentation: IAM Overview)
- Designing identity roles at the organization, folder, project, and resource level (Google Documentation: Using resource hierarchy for access control)
- Configuring Access Context Manager (Google Documentation: Access Context Manager Overview)
- Applying Policy Intelligence for better permission management (Google Documentation: Policy Intelligence overview)
- Managing permissions through groups (Google Documentation: Manage access to projects, folders, and organizations)
1.5 Defining resource hierarchy.
- Creating and managing organizations (Google Documentation: Creating and managing organizations)
- Managing organization policies for organization folders, projects, and resources (Google Documentation: Creating and managing organization policies)
- Using resource hierarchy for access control and permissions inheritance (Google Documentation: Using resource hierarchy for access control)
Topic 2: Securing communications and establishing boundary protection (21%)
2.1 Designing and configuring perimeter security. Considerations include:
- Configuring network perimeter controls (firewall rules, hierarchical firewalls, Identity-Aware Proxy [IAP], load balancers, and Certificate Authority Service) (Google Documentation: Setting up IAP for Compute Engine, Using IAP for TCP forwarding)
- Differentiating between private and public IP addressing (Google Documentation: IP addresses)
- Configuring web application firewall (Google Cloud Armor) (Google Documentation: Google Cloud Armor preconfigured WAF rules overview)
- Deploying Secure Web Proxy (Google Documentation: Deploy a Secure Web Proxy instance)
- Configuring Cloud DNS security settings (Google Documentation: Manage DNSSEC configuration)
- Continually monitoring and restricting configured APIs (Google Documentation: Introduction to the Cloud Monitoring API)
2.2 Configuring boundary segmentation. Considerations include:
- Configuring security properties of a VPC network, VPC peering, Shared VPC, and firewall rules (Google Documentation: VPC Network Peering)
- Configuring network isolation and data encapsulation for N-tier application design (Google Documentation: Best practices and reference architectures for VPC design)
- Configuring VPC Service Controls (Google Documentation: Overview of VPC Service Controls)
2.3 Establish private connectivity.
- Designing and configuring private connectivity between VPC networks and Google Cloud projects (Shared VPC, VPC peering, and Private Google Access for on-premises hosts) (Google Documentation: Configure Private Google Access for on-premises hosts)
- Designing and configuring private connectivity between data centers and VPC network (HA-VPN, IPsec, MACsec, and Cloud Interconnect) (Google Documentation: Cloud Interconnect overview)
- Establishing private connectivity between VPC and Google APIs (Private Google Access, Private Google Access for on-premises hosts, restricted Google access, Private Service Connect) (Google Documentation: Configuring Private Google Access, Private access options for services)
- Using Cloud NAT to enable outbound traffic (Google Documentation: Cloud NAT overview)
Topic 3: Ensuring data protection (20%)
3.1 Protecting sensitive data and preventing data loss. Considerations include:
- Inspecting and redacting personally identifiable information (PII) (Google Documentation: Classification, redaction, and de-identification, De-identifying sensitive data)
- Ensuring continuous discovery of sensitive data (structured and unstructured)
- Configuring pseudonymization (Google Documentation: Pseudonymization)
- Configuring format-preserving substitution (Google Documentation: Transformation reference)
- Restricting access to BigQuery, Cloud Storage, and Cloud SQL datastores (Google Documentation: Restrict access with column-level access control)
- Securing secrets with Secret Manager Secret Manager overview)
- Protecting and managing compute instance metadata About VM metadata)
3.2 Managing encryption at rest, in transit, and in use. Considerations include:
- Understanding the use cases for Google default encryption, customer-managed encryption keys (CMEK) including customer-supplied encryption keys (CSEK), Cloud External Key Manager (EKM), and Cloud HSM (Google Documentation: Encrypt disks with customer-supplied encryption keys, Customer-Supplied Encryption Keys, Customer managed encryption keys (CMEK))
- Creating and managing encryption keys for CMEK, CSEK, and EKM (Google Documentation: Customer-managed encryption keys (CMEK))
- Applying Google’s encryption approach to use cases (Google Documentation: Encryption in transit)
- Configuring object lifecycle policies for Cloud Storage (Google Documentation: Object Lifecycle Management)
- Enabling Confidential Computing (Google Documentation: Confidential VM)
3.3 Planning for security and privacy in AI. Considerations include:
- Implementing security controls for AI/ML systems (e.g., protecting against unintentional exploitation of data or models) (Google Documentation: Preventing Data Exfiltration)
- Determining security requirements for IaaS-hosted and PaaS-hosted training models
Topic 4: Managing operations (22%)
4.1 Automating infrastructure and application security. Considerations include:
- Automating security scanning for Common Vulnerabilities and Exposures (CVEs) through a continuous integration and delivery (CI/CD) pipeline (Google Documentation: Automatically scan workloads for known vulnerabilities)
- Configuring Binary Authorization to secure GKE clusters or Cloud Run (Google Documentation: Enable Binary Authorization for Cloud Run)
- Automating virtual machine image creation, hardening, maintenance, and patch management (Google Documentation: About Patch)
- Automating container image creation, verification, hardening, maintenance, and patch management (Google Documentation: Image management best practices)
- Managing policy and drift detection at scale (custom organization policies and custom modules for Security Health Analytics) (Google Documentation: Using custom modules with Security Health Analytics)
4.2 Configuring logging, monitoring, and detection. Considerations include:
- Configuring and analyzing network logs (firewall rule logs, VPC flow logs, packet mirroring, Cloud Intrusion Detection System [Cloud IDS], Log Analytics) (Google Documentation: VPC Flow Logs, Cloud IDS)
- Designing an effective logging strategy
- Logging, monitoring, responding to, and remediating security incidents (Google Documentation: Data incident response process)
- Designing secure access to logs (Google Documentation: Best practices for Cloud Audit Logs)
- Exporting logs to external security systems (Google Documentation: Scenarios for exporting Cloud Logging: Compliance requirements)
- Configuring and analyzing Google Cloud audit logs and data access logs (Google Documentation: Enable Data Access audit logs)
- Configuring log exports (log sinks and aggregated sinks) (Google Documentation: Collate and route organization- and folder-level logs to supported destinations)
- Configuring and monitoring Security Command Center (Google Documentation: Configure Security Command Center services)
Topic 5: Supporting compliance requirements (10%)
5.1 Determining regulatory requirements for the cloud. Considerations include:
- Determining concerns relative to compute, data, and network
- Evaluating the security shared responsibility model (Google Documentation: Shared responsibilities and shared fate on Google Cloud)
- Configuring security controls within cloud environments to support compliance requirements (regionalization of data and services) (Google Documentation: Regionalization and data residency)
- Restricting compute and data for regulatory compliance (Assured Workloads, organizational policies, Access Transparency, Access Approval) (Google Documentation: Assured Workloads, Access Transparency)
- Determining the Google Cloud environment in scope for regulatory compliance
2. Explore Learning Resources
We cannot stress enough that only finding the right learning resources will allow you to understand each and every domain properly. Choosing the right resources with reliable content is very important. As a matter of fact, there are various resources to choose from. This makes it difficult to select the authentic and genuine ones. Here we provide you quick links to some of the Learning Resources you need to ace the exam:
– Google Professional Cloud Security Engineer Training
Google provides training to candidates with the Security in Google Cloud Platform course. This course gives candidates a good understanding of the security controls and techniques on Google Cloud Platform. This provides lectures, demonstrations, and hands-on labs and helps candidates to explore and deploy the components of a secure Google Cloud solution.
– Hands-on practice
The Professional Cloud Security Engineer exam is designed to test technical skills related to the job role. So, candidates must have hands-on experience to have the best preparation for the exam. Google cloud provides candidates both experience or practice with their hands-on labs available on Qwiklabs. Moreover, to level up their skills and knowledge they include:
- Firstly, Google Cloud Free Tier
- Secondly, Security and Identity Fundamental
– Hands on Lab
Networking is a principle theme of cloud computing that is the underlying structure of Google Cloud. This connects all resources and services to one another. This covers essential Google Cloud networking services and will give candidates hands-on practice with specialized tools for developing mature networks. Also, they will learn about VPCs, for creating enterprise-grade load balancers. However, Networking in the Google Cloud will give the practical experience needed so you can start building robust networks right away.
Hands-on labs: Networking in the Google Cloud
3. Online Tutorials and Study Guides
Online Tutorials enhance you knowledge and provide in depth understanding about the exam concepts. Moreover, Study Guides will be your support throughout your journey towards the exam. These resources will help you stay consistent and determined. Also, they enrich your learning experience.
4. Practice Tests to analyse your performance
The Google Professional Cloud Security Engineer Practice Exams constitute a vital component of your Cheat Sheet. In other words, these practice tests are indispensable, as they enable you to identify your areas of weakness and strength. Furthermore, consistent practice enhances your ability to answer questions efficiently, ultimately saving time during the actual exam. It is advisable to commence practicing after completing an entire topic, as this serves as an effective revision strategy. Therefore, it is crucial to locate top-quality practice resources. Let’s Start Practising Now!