The MS-500: Microsoft 365 Security Administration certification verifies your skills to proactively secure Microsoft 365 enterprise environments and your ability to respond, perform investigations, and enforce data governance. If you are planning to take this test, make sure that you are very familiar with both on-premises and cloud versions of Microsoft 365. You will need to have experience using tools for investigating attacks like Azure Security Center, Office 365 Advanced Threat Protection (ATP), Dynamic Access Control (DAC), and Windows Defender Advanced Threat Protection (Windows Defender ATP).
About Microsoft: MS-500 Exam
The MS-500: Microsoft 365 Security Administrator is a skilled and knowledgeable expert who proactively secures the enterprise environment, detects threats, and enforces data governance while uncovering security incidents and security violations.
The role of the Microsoft 365 Security Administrator incorporates responsibilities of various job roles under the MCSA Security track, including but not limited to: Security Administrator, Forefront Identity Manager Administrator, Forefront Server Protection Administrator, and others. The Microsoft 365 Security Administrator sees that security policies are adhered to and that they meet regulatory compliance. He plays a critical role in sustaining an organization’s ecosystem while protecting customer and employee data from cyber threats. Therefore, it is very important to understand the ms-500 exam difficulty level as well as the complete MS-500 exam guide for better results.
Microsoft: MS-500 Exam Guide
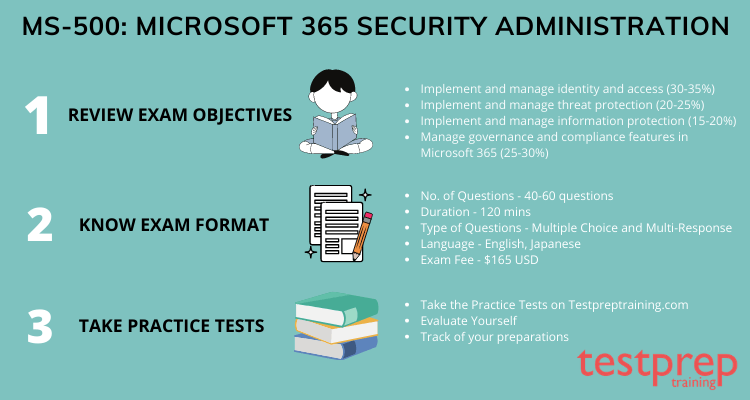
Being crystal clear with the format of the exam makes it quite easy to plan for the same and perform better –
- In the Microsoft MS-500 exam, expect 40 to 60 questions within a 120-minute timeframe, requiring quick responses.
- There are no negative markings, so feel free to attempt all questions without worry.
- The exam fee for Microsoft MS-500 is $165 USD, and the passing score is 700 on a scale of 1-1000.
- The exam questions follow a format of multiple-choice and multiple-response. We suggest using the elimination technique to narrow down options and choose the best match. So, eliminate options that don’t fit the requirement and go for the most suitable one.
MS-500 Exam Topics
Each question aims to test your knowledge, so it’s crucial to have a deep understanding of the course outline. The sections covered in the Microsoft MS-500 exam are outlined below.
Course Outline for Microsoft MS-500 Exam was updated on November 4, 2022.
1. Implement and manage identity and access (25-30%)
Plan and implement identity and access for Microsoft 365 hybrid environments
- Choose an authentication method to connect to a hybrid environment (Microsoft documentation: Choose the right authentication method for your Azure AD Hybrid)
- Plan and implement pass-through authentication and password hash sync (Microsoft documentation: Implement password hash synchronization, Pass-through Authentication)
- Plan and implement Azure AD synchronization for hybrid environments (Microsoft documentation: Configure hybrid Azure AD join, Plan your hybrid Azure Active Directory join implementation)
- Monitor and troubleshoot Azure AD Connect events (Microsoft documentation: Troubleshoot Azure AD Connect connectivity issues, Troubleshoot object synchronization with Azure AD Connect sync)
Plan and implement Identities in Azure AD
- Implement Azure AD group membership (Microsoft documentation: Create a basic group and add members using Azure Active Directory)
- Implement password management, including self-service password reset and Azure AD password protection (Microsoft documentation: Plan an Azure Active Directory self-service password reset deployment)
- Manage external identities in Azure AD and Microsoft 365 workloads (Microsoft documentation: External Identities in Azure Active Directory)
- Plan and implement roles and role groups
- Audit Azure AD
Implement authentication methods
- Implement multi-factor authentication (MFA) by using conditional access policies (Microsoft documentation: Conditional Access: Require MFA for all users)
- Manage and monitor MFA (Microsoft documentation: Manage user authentication methods for Azure AD Multi-Factor Authentication)
- Plan and implement Windows Hello for Business, FIDO, and passwordless authentication
Plan and implement conditional access
- Plan and implement conditional access policies (Microsoft documentation: Plan a Conditional Access deployment)
- Plan and implement device compliance policies (Microsoft documentation: Use compliance policies to set rules for devices)
- Test and troubleshoot conditional access policies (Microsoft documentation: Troubleshooting Conditional Access using the What If tool)
Configure and manage identity governance
- Implement Azure AD Privileged Identity Management (Microsoft documentation: Azure AD Privileged Identity Management)
- Implement and manage entitlement management (Microsoft documentation: Azure AD entitlement management)
- Implement and manage access reviews (Microsoft documentation: Azure AD access reviews)
Implement Azure AD Identity Protection
- Implement user risk policy (Microsoft documentation: Configure and enable risk policies)
- Implement sign-in risk policy (Microsoft documentation: Use risk detections for user sign-ins to trigger Azure AD Multi-Factor Authentication)
- Configure Identity Protection alerts (Microsoft documentation: Azure Active Directory Identity Protection notifications)
- Review and respond to risk events (Microsoft documentation: Remediate risks and unblock users)
2. Implement and manage threat protection (30-35%)
Secure identity by using Microsoft Defender for Identity
- Plan a Microsoft Defender for Identity solution (Microsoft documentation: Plan capacity for Microsoft Defender for Identity)
- Install and configure Microsoft Defender for Identity (Microsoft documentation: Install the Microsoft Defender for Identity sensor)
- Manage and monitor Microsoft Defender for Identity (Microsoft documentation: Microsoft Defender for Identity monitored activities)
- Secure score
- Analyze identity-related threats and risks identified in Microsoft 365 Defender
Secure endpoints by using Microsoft Defender for Endpoint
- Plan a Microsoft Defender for Endpoint solution (Microsoft documentation: Plan your Microsoft Defender for Endpoint deployment)
- Implement Microsoft Defender for Endpoint (Microsoft documentation: Set up and configure Microsoft Defender for Endpoint Plan 1)
- Manage and monitor Microsoft Defender for Endpoint (Microsoft documentation: Microsoft Defender for Endpoint)
- Analyze and remediate threats and risks to endpoints identified in Microsoft 365 Defender
Secure endpoints by using Microsoft Endpoint Manager
- Plan for device and application protection (Microsoft documentation: App protection policies overview)
- Configure and manage Microsoft Defender Application Guard (Microsoft documentation: Application Guard Application Guard testing scenarios)
- Configure and manage Microsoft Defender Application Control (Microsoft documentation: Windows Defender Application Control management with Configuration Manager)
- Configure and manage exploit protection (Microsoft documentation: Enable exploit protection)
- Configure and manage device encryption (Microsoft documentation: Overview of BitLocker Device Encryption in Windows)
- Implement application protection policies (Microsoft documentation: How to create and assign app protection policies)
- Monitor and manage device security status using Microsoft Endpoint Manager admin center (Microsoft documentation: Walkthrough Microsoft Intune admin center, Manage devices with endpoint security in Microsoft Intune)
- Analyze and remediate threats and risks to endpoints identified in Microsoft Endpoint Manager (Microsoft documentation: Enforce compliance for Microsoft Defender, Overview of automated investigations)
Secure collaboration by using Microsoft Defender for Office 365
- Plan a Microsoft Defender for Office 365 solution
- Configure Microsoft Defender for Office 365 (Microsoft documentation: Microsoft Defender for Office 365)
- Monitor for threats using Microsoft Defender for Office 365 (Microsoft documentation: Threat investigation and response)
- Analyze and remediate threats and risks to collaboration workloads identified in Microsoft 365 Defender (Microsoft documentation: Threat investigation and response)
- Conduct simulated attacks using Attack simulation training (Microsoft documentation: Get started using Attack simulation training in Defender for Office 365)
Detect and respond to threats in Microsoft 365 by using Microsoft Sentinel
- Plan a Microsoft Sentinel solution for Microsoft 365 (Microsoft documentation: What is Microsoft Sentinel?)
- Implement and configure Microsoft Sentinel for Microsoft 365 (Microsoft documentation: Onboard Microsoft Sentinel)
- Manage and monitor Microsoft 365 security by using Microsoft Sentinel
- Respond to threats using built-in playbooks in Microsoft Sentinel (Microsoft documentation: Use playbooks with automation rules in Microsoft Sentinel)
Secure connections to cloud apps by using Microsoft Defender for Cloud Apps
- Plan Microsoft Defender for Cloud Apps implementation (Microsoft documentation: Get started with Microsoft Defender for Cloud Apps)
- Configure Microsoft Defender for Cloud Apps (Microsoft documentation: Microsoft Defender for Endpoint integration with Microsoft Defender for Cloud Apps)
- Manage cloud app discovery (Microsoft documentation: Set up Cloud Discovery)
- Manage entries in the Microsoft Defender for Cloud Apps catalog (Microsoft documentation: Working with App risk scores)
- Manage apps in Microsoft Defender for Cloud Apps (Microsoft documentation: Microsoft Defender for Cloud Apps overview)
- Configure Microsoft Defender Cloud Apps connectors and OAuth apps (Microsoft documentation: OAuth app policies)
- Configure Microsoft Defender for Cloud Apps policies and templates (Microsoft documentation: Get started with Microsoft Defender for Cloud Apps)
- Analyze and remediate threats and risks relating to cloud app connections identified in Microsoft 365 Defender
- Manage App governance in Microsoft Defender for Cloud Apps
3. Implement and manage information protection (15-20%)
Manage sensitive information
- Plan a sensitivity label solution (Microsoft documentation: Learn about sensitivity labels)
- Create and manage sensitive information types (Microsoft documentation: Create custom sensitive information types in the Compliance center)
- Configure sensitivity labels and policies. (Microsoft documentation: Create and configure sensitivity labels and their policies)
- Publish sensitivity labels to Microsoft 365 workloads
- Monitor data classification and label usage by using Content explorer and Activity explorer (Microsoft documentation: Get started with content explorer, Get started with activity explorer)
- Apply labels to files and schematized data assets in Microsoft Purview Data Map (Microsoft documentation: Labeling in the Microsoft Purview Data Map)
Implement and manage Microsoft Purview Data Loss Prevention (DLP)
- Plan a DLP solution (Microsoft documentation: Learn about data loss prevention)
- Create and manage DLP policies for Microsoft 365 workloads (Microsoft documentation: Create a DLP policy from a template)
- Implement and manage Endpoint DLP (Microsoft documentation: Learn about Endpoint data loss prevention)
- Monitor DLP
- Respond to DLP alerts and notifications (Microsoft documentation: Configure and view alerts for data loss prevention polices, Send email notifications and show policy tips for DLP policies)
Plan and implement Microsoft Purview Data lifecycle management
- Plan for data lifecycle management (Microsoft documentation: Get started with data lifecycle management)
- Review and interpret data lifecycle management reports and dashboards (Microsoft documentation: How to use the Microsoft data classification dashboard)
- Configure retention labels, policies, and label policies (Microsoft documentation: Create and configure retention policies)
- Plan and implement adaptive scopes
- Configure retention in Microsoft 365 workloads (Microsoft documentation: Manage data retention in Microsoft 365 workloads)
- Find and recover deleted Office 365 data (Microsoft documentation: Recover deleted messages in a user’s mailbox in Exchange Online)
4. Manage compliance in Microsoft 365 (20- 25%)
Manage and analyze audit logs and reports in Microsoft Purview
- Plan for auditing and reporting (Microsoft documentation: Auditing solutions in Microsoft Purview)
- Investigate compliance activities by using audit logs (Microsoft documentation: Microsoft Purview Audit (Premium), Search the audit log in the compliance portal)
- Review and interpret compliance reports and dashboards (Microsoft documentation: Improve your regulatory compliance, How to use the Microsoft data classification dashboard)
- Configure alert policies (Microsoft documentation: Alert policies in Microsoft 365)
- Configure audit retention policies (Microsoft documentation: Manage audit log retention policies)
Plan for, conduct, and manage eDiscovery cases
- Recommend eDiscovery Standards or Premium (Microsoft documentation: Microsoft Purview eDiscovery solutions)
- Plan for content search and eDiscovery (Microsoft documentation: Create a content search, Microsoft Purview eDiscovery solutions)
- Delegate permissions to use search and discovery tools (Microsoft documentation: Assign eDiscovery permissions in the compliance portal, Assign eDiscovery permissions in Exchange Online)
- Use search and investigation tools to discover and respond
- Manage eDiscovery cases (Microsoft documentation: Create and manage an eDiscovery (Premium) case)
Manage regulatory and privacy requirements
- Plan for regulatory compliance in Microsoft 365 (Microsoft documentation: Microsoft 365 guidance for security & compliance, Microsoft Purview Compliance Manager)
- Manage regulatory compliance in the Microsoft Purview Compliance Manager (Microsoft documentation: Get started with Compliance Manager)
- Implement privacy risk management in Microsoft Priva (Microsoft documentation: Learn about Priva Privacy Risk Management)
- Implement and manage Subject Rights Requests in Microsoft Priva (Microsoft documentation: Learn about Priva Subject Rights Requests)
Manage insider risk solutions in Microsoft 365
- Implement and manage Customer Lockbox (Microsoft documentation: Microsoft Purview Customer Lockbox)
- Implement and manage communication compliance policies (Microsoft documentation: Create and manage communication compliance policies)
- Implement and manage Insider risk management policies (Microsoft documentation: Get started with insider risk management)
- Implement and manage information barrier policies (Microsoft documentation: Get started with information barriers)
- Implement and manage privileged access management (Microsoft documentation: Learn about privileged access management)
For more details and quick revision refer MS-500 Study Guide and MS-500 Cheat Sheet Now!
MS-500: Microsoft 365 Security Administration Study Guide
Selecting the proper and the most accurate study material is half battle itself, so choose your study material very efficiently. Also, go through MS-500 Microsoft 365 Security Administration study guide as it the road map for your success in the examination. Proper planning is a must, and it can be only done if you know your syllabus accurately. Go through the course outline very thoroughly as having a reasonable comprehension of your course will truly assist you in different areas. It will surely make a change and can also increase your opportunity to crack this certification exam.
Use the Microsoft MS-500 Cheat Sheet to get quick overview about the Exam!
You can go for instructor-led training, to get your concepts clear and the MS-500 training is really beneficial. Moreover, it is the best learning environment for promoting focus and concentration among the candidates. You should also join Microsoft Community, as will definitely maximize your learning. It is the best place to swap ideas and learn from others. It will help you to solidify and clarify your course syllabus and in addition to it, it will also bring confidence and will make you motivated to do better in the exam.
Appear for the practice tests, as being placed in the same situation and having the feeling of the same amount of pressure before the actual exam will be really beneficial and will boost your confidence. Further, you can get authentic study materials on the official website of Microsoft. Stick to the official website for the study-related materials as those will be more accurate and authentic than the ones provided by any other websites.
Have the right strategy and also the right planning to clear the exam. Finally, we present our Microsoft: MS-500 Online Tutorial to ease your preparation, by serving as a roadmap containing a list of all the necessary study resources. These resources will help you a lot in the preparation for the exam
How to prepare for the MS-500 Exam: Microsoft 365 Security Administration?
Expert’s Corner
The MS-500 Microsoft 365 Security Administration exam is meant for those who have a strong command over anti-virus, anti-malware, and other security solutions for servers as well as client computers running Microsoft 365. Also, you can use this certification on your resume in lieu of an MCSE or MCTS certification when you do not need these additional designations. If you will prepare for this exam with full dedication you can really clear it easily. Take practice tests seriously and solve as much as possible. With the help of it, you’ll get to estimate your timings as well. Moreover, it is the key determinant in deciding the success of the candidates in the professional exams. Do appear for the exam with full confidence. Take the Microsoft MS-500 Free Practice Test Now!



