Cloud security has exploded in popularity in recent years. As a result, Cloud specialists are in high demand these days, and competence in this field could not be more valuable. Furthermore, when it comes to cloud security, the terms Certificate of Cloud Security Knowledge (CCSK) and Certified Cloud Security Professional (CCSP) are frequently used. They are both among the best cloud security certifications available, and they provide comprehensive training in cloud security principles.
However, the questions that generally pop up include,
- Firstly, Are the two certifications the same or entirely different?
- Secondly, What is the primary differences between CCSK and CCSP?
- Thirdly, Which one should I choose?
So, let’s delve into the answers to these questions to better comprehend the comparison between CCSK and CCSP.
CCSK Vs CCSP: A Comprehensive Comparison
In fact, neither the CCSK nor the CCSP is competing or related certificates. They are, nonetheless, both among the top cloud security certifications, with fundamentally different cloud security objectives for a student. The Certificate of Cloud Security Knowledge (CCSK) is a certification program that educates individuals about cloud security issues. This certification involves a knowledge assessment covering three main aspects: CSA guidance, CSA cloud control matrix, and ENISA report.
However, the CCSP certification goes beyond just testing theoretical knowledge of security features. It also evaluates practical skills and real-world experience. This certification acknowledges both the acquired knowledge and practical expertise, earning the individual the title of a “professional” in the field. Before you slide into CCSK and CCSP Certification, it is highly important to know what exam actually is. Therefore, let’s give a quick look at the CCSK and CCSP exam breakdown.
CCSK – EXAM DETAILS
The first and foremost point for taking the CCSK exam is to understand the basic structure, offerings, purpose, and eligibility. Therefore, it becomes crucial to understand for whom is this certification suitable.

Who Earns the CCSK?
CCSK certification exam is the best fit for individuals who have an interest in the field of cloud technology. That is to say, people who are working in the field of Information security, manager, security consultant, etc can take the exam.
Exam Overview
The CCSK exam evaluates a wide understanding of cloud security. It covers various subjects like architecture, compliance, encryption, operations, and more, providing a comprehensive overview.
Exam Details
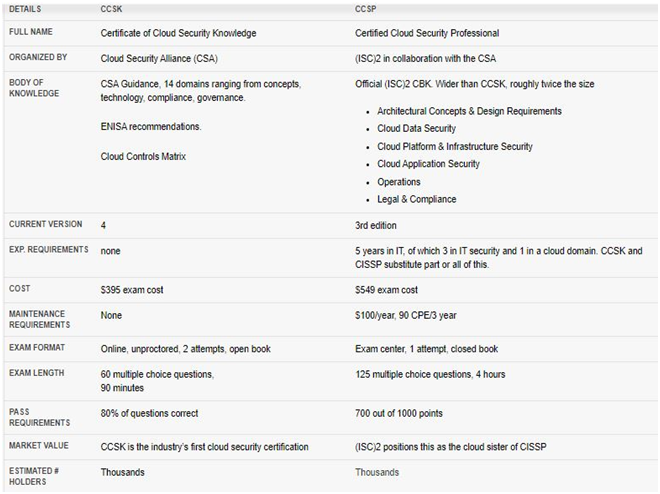
CCSK exam comprises 60 questions that are to be completed in a time period of 90 minutes. The exam is a multiple-choice and multiple responsive questions that you take online. Further, you have to score at least 80% to pass the exam. The exam is available in the English language. Above all, the exam costs $395 USD.
Prerequisites for the exam
CCSK exam will examine you on the following abilities.
- To begin, having a solid grasp of cloud security and technical aspects is essential.
- Next, the capability to create a universally applicable cloud security program.
- Finally, a strong understanding of cloud computing is also crucial.

CCSK Course Outline
CCSK covers six modules which are as follows:
FIRST MODULE – Cloud Architecture
- First, you should have a good understanding of the virtualization role and framework for cloud security
- Second, you should have a good understanding of the cloud computing models for delivery and security
SECOND MODULE – Infrastructure Security for Cloud
- First, you should have good knowledge of management interfaces, cloud components, and networks
- Second, thorough understanding of virtual networking and workloads concepts including basics of serverless and containers
THIRD MODULE – Managing Cloud Security and Risk
- First, you should have knowledge of the security part of cloud security
- Second, provides an overview of risk assessment and governance
FOURTH MODULE – Cloud Computing Data Security
- First, you will get an overview of the life cycle management of cloud and applying security controls
- Second, topics include cloud storage model, data security lifecycle and BYOK
FIFTH MODULE – Application Security and Identity Management for Cloud Computing
- First, you should have information about application management and identity management of cloud deployment
- Second, topics include secure development, managing cloud application security
SIXTH MODULE – Cloud Security Operations
- First, you should have a good understanding of evaluating, managing cloud computing and selecting providers
- Second, it elaborates the security role and impact of cloud on incident response
CCSP – EXAM DETAILS
We will now elaborate on some of the important exam features and requirements for preparing the CCSP exam.

Who Earns the CCSP?
The CCSP certification is an excellent choice for IT and information security leaders who want to demonstrate their grasp of cybersecurity and protecting important assets in the cloud.
Exam Overview
The Certified Cloud Security Professional (CCSP) exam is a prominent certification offered by (ISC)². This course is designed to help you counteract security risks to your cloud storage by:
- Firstly, understanding the potential information security risks.
- Secondly, gaining in-depth knowledge of implementing strategies to uphold data security.
Exam Overview
Since it is always considered good to have exam details beforehand. So, here it is. In general, the CCSP exam is intense and can take you three hours to complete. The exam comprises 125 multiple-choice questions and is available in the English language. Further, you need to accumulate a score of 700 or more. Most importantly, the exam will cost you $599 USD.
Prerequisites for the Exam
To begin your voyage in the CCSP certification course, you must have:
- Firstly, the candidate must have at least five years of working experience in IT, including three years of information security and one year of cloud security experience
- Secondly, a candidate who lacks the required experience to become a CCSP may become an Associate of (ISC)² by successfully passing the CCSP examination. After that, the Associate of (ISC)² will have 6 years to earn the 5 years required experience.
CCSP Course Outline
The CCSP exam appraises your expertise across six security domains. Therefore, think of the following domains as topics you need to master.
Domain 1: Cloud Concepts, Architecture and Design 17%
Understand Cloud Computing Concepts
- Cloud computing definitions
- Cloud computing roles and responsibilities (e.g., cloud service customer, cloud service provider, cloud service partner, cloud service broker, regulator)
- Key cloud computing characteristics (e.g., on-demand self-service, broad network access, multi-tenancy, rapid elasticity and scalability, resource pooling, measured service)
- Building block technologies (e.g., virtualization, storage, networking, databases, orchestration)
Describe Cloud Reference Architecture
- Cloud Computing Activities
- Cloud Service Capabilities (e.g., application capability types, platform capability types, infrastructure capability types)
- Then, Cloud Service Categories, Infrastructure as a Service (IaaS), Platform as a Service (PaaS))
- Cloud deployment models (e.g., public, private, hybrid, community, multi-cloud)
- Cloud shared considerations (e.g., interoperability, portability, reversibility, availability, security, privacy, resiliency, performance, governance, maintenance and versioning, service levels and service-level agreements (SLA), auditability, regulatory, outsourcing)
- Impact of related technologies (e.g., data science, machine learning, artificial intelligence (AI), blockchain, Internet of Things (IoT), containers, quantum computing, edge computing, confidential computing, DevSecOps)
Understand Security Concepts Relevant to Cloud Computing
- Cryptography and key management
- Identity and access control (e.g., user access, privilege access, service access)
- Data and media sanitization (e.g., overwriting, cryptographic erase)
- Network security (e.g., network security groups, traffic inspection, geofencing, zero trust network)
- Virtualization security (e.g., hypervisor security, container security, ephemeral computing, serverless technology)
- Common threats
- Security hygiene (e.g., patching, baselining)
Understand the Design Principles of Secure Cloud Computing
- Cloud secure data lifecycle
- Cloud-based business continuity (BC) and disaster recovery (DR) plan
- Business impact analysis (BIA) (e.g., cost-benefit analysis, return on investment (ROI))
- Functional security requirements (e.g., portability, interoperability, vendor lock-in)
- Security considerations and responsibilities for different cloud categories (e.g., Software as a Service (SaaS), Infrastructure as a Service (IaaS), Platform as a Service (PaaS))
- Cloud design patterns (e.g., SANS security principles, Well-Architected Framework, Cloud Security Alliance (CSA) Enterprise Architecture)
- DevOps security
Evaluate Cloud Service Providers
- Verification against criteria (e.g., International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 27017, Payment Card Industry Data Security Standard (PCI DSS))
- System/subsystem product certifications (e.g., Common Criteria (CC), Federal Information Processing Standard (FIPS) 140-2)
Domain 2: Cloud Data Security 20%
Describe Cloud Data Concepts
- Cloud Data Life Cycle Phases
- Data Dispersion
- Data flows
Design and Implement Cloud Data Storage Architectures
- Storage types (e.g., long-term, ephemeral, raw storage)
- Threats to storage types
Design and Apply Data Security Technologies and Strategies
- Encryption and key management
- Hashing
- Data obfuscation (e.g., masking, anonymization)
- Tokenization
- Data loss prevention (DLP)
- Keys, secrets and certificates management
Implement Data Discovery
- Structured data
- Unstructured data
- Semi-structured data
- Data location
Implement Data Classification
- Data classification policies
- Data mapping
- Data labeling
Design and Implement Information Rights Management (IRM)
- Objectives (e.g., data rights, provisioning, access models)
- Appropriate Tools (e.g., issuing and revocation of certificates)
Plan and Implement Data Retention, Deletion and Archiving Policies
- Data Retention Policies
- Then, Data Deletion Procedures and Mechanisms
- Data Archiving Procedures and Mechanisms
- Legal Hold
Design and Implement Auditability, Traceability and Accountability of Data Events
- Definition of Event Sources and Requirement of Identity Attribution
- Logging, Storage and Analysis of Data Events
- Chain of Custody and Non-repudiation
Domain 3: Cloud Platform & Infrastructure Security 17%
Comprehend Cloud Infrastructure Components
- Physical Environment
- Network and Communications
- Compute
- Virtualization
- Storage
- Management Plane
Design a Secure Data Center
- Logical Design (e.g., tenant partitioning, access control)
- Physical Design (e.g. location, buy or build)
- Environmental design (e.g., Heating, Ventilation, and Air Conditioning (HVAC), multi-vendor pathway connectivity)
- Design resilient
Analyze Risks Associated with Cloud Infrastructure
- Risk Assessment and Analysis
- Cloud Vulnerabilities, Threats and Attacks
- Risk mitigation strategies
Design and Plan Security Controls
- Physical and environmental protection (e.g., on-premises)
- System, storage and communication protection
- Identification, authentication and authorization in cloud environments
- Audit mechanisms (e.g., log collection, correlation, packet capture)
Plan Disaster Recovery (DR) and Business Continuity (BC)
- Business continuity (BC) / disaster recovery (DR) strategy
- Business requirements (e.g., Recovery Time Objective (RTO), Recovery Point Objective (RPO), recovery service level)
- Creation, implementation and testing of plan
Domain 4: Cloud Application Security 17%
Advocate Training and Awareness for Application Security
- Cloud Development Basics
- Common Pitfalls
- Common Cloud vulnerabilities (e.g., Open Web Application Security Project (OWASP) Top-10, SANS Top-25)
Describe the Secure Software Development Life Cycle (SDLC) Process
- Business Requirements
- Phases and methodologies (e.g., design, code, test, maintain, waterfall vs. agile)

Apply the Secure Software Development Life Cycle (SDLC)
- Cloud-specific risks
- Threat modeling (e.g., Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege (STRIDE), Damage, Reproducibility, Exploitability, Affected Users, and Discoverability (DREAD), Architecture, Threats, Attack Surfaces, and Mitigations (ATASM), Process for Attack Simulation and Threat Analysis (PASTA))
- Avoid common vulnerabilities during development
- Secure coding (e.g., Open Web Application Security Project (OWASP) Application Security
- Verification Standard (ASVS), Software Assurance Forum for Excellence in Code (SAFECode))
- Software configuration management and versioning
Apply Cloud Software Assurance and Validation
- Functional and non-functional testing
- Security testing methodologies (e.g., blackbox, whitebox, static, dynamic, Software Composition Analysis (SCA), interactive application security testing (IAST))
- Quality assurance (QA)
- Abuse case testing
Use Verified Secure Software
- Securing application programming interfaces (API)
- Supply-chain management (e.g., vendor assessment)
- Third-party software management (e.g., licensing)
- Validated open-source software
Comprehend the Specifics of Cloud Application Architecture
- Supplemental security components (e.g., web application firewall (WAF), Database Activity Monitoring (DAM), Extensible Markup Language (XML) firewalls, application programming interface (API) gateway)
- Cryptography
- Sandboxing
- Application virtualization and orchestration (e.g., microservices, containers)
Design Appropriate Identity and Access Management (IAM) Solutions
- Federated identity
- Identity providers (IdP)
- Single sign-on (SSO)
- Multi-factor authentication (MFA)
- Cloud access security broker (CASB)
- Secrets management
Domain 5: Cloud Security Operations 16%
Implement and Build Physical and Logical Infrastructure for Cloud Environment »
- Hardware specific security configuration requirements (e.g., hardware security module (HSM) and Trusted Platform Module (TPM))
- Installation and configuration of management tools
- Virtual hardware specific security configuration requirements (e.g., network, storage, memory, central processing unit (CPU), Hypervisor type 1 and 2)
- Installation of guest operating system (OS) virtualization toolsets
Operate Physical and Logical Infrastructure for Cloud Environment
- Access controls for local and remote access (e.g., Remote Desktop Protocol (RDP), secure terminal access, Secure Shell (SSH), console-based access mechanisms, jumpboxes, virtual client)
- Secure network configuration (e.g., virtual local area networks (VLAN), Transport Layer Security (TLS), Dynamic Host Configuration Protocol (DHCP), Domain Name System Security Extensions (DNSSEC), virtual private network (VPN))
- Network security controls (e.g., firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), honeypots, vulnerability assessments, network security groups, bastion host)
- Operating system (OS) hardening through the application of baselines, monitoring and remediation (e.g., Windows, Linux, VMware)
- Patch management
- Infrastructure as Code (IaC) strategy
- Availability of clustered hosts (e.g., distributed resource scheduling, dynamic optimization, storage clusters, maintenance mode, high availability (HA))
- Availability of guest operating system (OS)
- Performance and capacity monitoring (e.g., network, compute, storage, response time)
- Hardware monitoring (e.g., disk, central processing unit (CPU), fan speed, temperature)
- Configuration of host and guest operating system (OS) backup and restore functions
- Management plane (e.g., scheduling, orchestration, maintenance)
Implement operational controls and standards (e.g., Information Technology Infrastructure Library (ITIL), International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 20000-1)
- Incident management
- Problem management
- Release management
- Deployment management
- Configuration management
- Service level management
- Availability management
- Capacity management
Support Digital Forensics
- Forensic Data Collection Methodologies
- Evidence Management
- Collect, Acquire and Preserve Digital Evidence
Manage Communication with Relevant Parties
- Vendors
- Customers
- Partners
- Regulators
- Other Stakeholders
Manage Security Operations
- Forensic data collection methodologies
- Evidence management
- Collect, acquire, and preserve digital evidence
- Security operations center (SOC)
- Intelligent monitoring of security controls (e.g., firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), honeypots, network security groups, artificial intelligence (AI))
- Log capture and analysis (e.g., security information and event management (SIEM), log management)
- Incident management
- Vulnerability assessments
Domain 6: Legal, Risk and Compliance 13%
Articulate Legal Requirements and Unique Risks within the Cloud Environment
- Conflicting international legislation
- Evaluation of legal risks specific to cloud computing
- Legal framework and guidelines
- eDiscovery (e.g., International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 27050, Cloud Security Alliance (CSA) Guidance)
- Forensics requirements

Understand Privacy Issues
- Difference between contractual and regulated private data (e.g., protected health information (PHI), personally identifiable information (PII))
- Country-specific legislation related to private data (e.g., protected health information (PHI), personally identifiable information (PII))
- Jurisdictional differences in data privacy
- Standard privacy requirements (e.g., International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 27018, Generally Accepted Privacy Principles (GAPP), General Data Protection Regulation (GDPR))
- Privacy Impact Assessments (PIA)
Understand Audit Process, Methodologies, and Required Adaptations for a Cloud Environment
- Internal and external audit controls
- Impact of audit requirements
- Identify assurance challenges of virtualization and cloud
- Types of audit reports (e.g., Statement on Standards for Attestation Engagements (SSAE), Service Organization Control (SOC), International Standard on Assurance Engagements (ISAE))
- Restrictions of audit scope statements (e.g., Statement on Standards for Attestation Engagements (SSAE), International Standard on Assurance Engagements (ISAE))
- Gap analysis (e.g., control analysis, baselines)
- Audit planning
- Internal information security management system
- Internal information security controls system
- Policies (e.g., organizational, functional, cloud computing)
- Identification and involvement of relevant stakeholders
- Specialized compliance requirements for highly-regulated industries (e.g., North American Electric Reliability Corporation / Critical Infrastructure Protection (NERC / CIP), Health Insurance Portability and Accountability Act (HIPAA), Health Information Technology for Economic and Clinical Health (HITECH) Act, Payment Card Industry (PCI))
- Impact of distributed information technology (IT) model (e.g., diverse geographical locations and crossing over legal jurisdictions)
Understand the Implications of Cloud to Enterprise Risk Management
- Assess providers risk management programs (e.g., controls, methodologies, policies, risk profile, risk appetite)
- Difference between data owner/controller vs. data custodian/processor
- Regulatory transparency requirements (e.g., breach notification, Sarbanes-Oxley (SOX), General Data Protection Regulation (GDPR))
- Risk treatment (i.e., avoid, mitigate, transfer, share, acceptance)
- Different risk frameworks
- Metrics for risk management
- Assessment of risk environment (e.g., service, vendor, infrastructure, business)
Understand Outsourcing and Cloud Contract Design
- Business requirements (e.g., service-level agreement (SLA), master service agreement (MSA), statement of work (SOW))
- Vendor management (e.g., vendor assessments, vendor lock-in risks, vendor viability, escrow)
- Contract management (e.g., right to audit, metrics, definitions, termination, litigation, assurance, compliance, access to cloud/data, cyber risk insurance)
- Supply-chain management (e.g., International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 27036)
Both the certifications are elaborated above for a much better and clear understanding. Therefore, its time you heed to the primary differences between these two.
Primary Differences between CCSK and CSSP
Apparently, CCSK and CCSP differ from each other. Saying so, follow the points that distinguish the two.

Knowledge Gained
CCSK certification involves learning from CSA guidance, CSA cloud control matrix, and ENISA document. It helps learners build a substantial knowledge base through the certification course. In contrast, CCSP emphasizes both knowledge acquisition and application. This enables professionals to deeply understand their work and retain that understanding.
Examination keys
The CCSK exam focuses on multiple-choice questions on the focussed domain under the certification. On the other hand, the CCSP exam analyses both knowledge and practice. That is to say, the exam comprises both MCQs as well as reality posed problem-solving questions for the learners.
Conducting the exam
The CCSK certification is an online exam, and the candidates can attempt it from anywhere using an internet connection. Further, it allows two to attempt the certification exam with one registration.
The CCSP exam takes place at the test center of PearsonVUE. Unlike CCSK, only a single attempt at the examination is possible on registering.
Maintenance of earned certificate
Additionally, the CCSK exam doesn’t need ongoing maintenance. Professionals aren’t required to pay extra yearly fees or submit additional CPEs. In contrast, the CCSP exam involves an annual maintenance fee of $100 and the need to earn 90 CPEs.
CCSK vs CCSP: Which Certification is the Best?
Your certification should be based on your field of work. If you are a newbie looking to start a career in the cloud security field, CCSK will be the best option for you. Not only does the CCSK certification provide appropriate cloud knowledge, but it also allows you to engage in a variety of cloud security activities. Furthermore, CCSK is solely focused on cloud security, architectural patterns, and cloud-specific technologies, all of which aid in gaining a deeper understanding. I also love how it is seen in a shorter period of time.
But if you have the time and means, considering both is a good option. You could start with CCSK certification and then proceed to CCSP (remember, CCSK also counts as 1 year of experience for CCSP). The only mistake here would be not pursuing either of them.
Expert’s Corner
In summary, CCSP and CCSK certifications complement each other in several ways. They offer distinct levels of cloud security knowledge and can be pursued to enhance your understanding of cloud computing and its security measures. These certifications are helpful for assessing your skills, requirements, and familiarity with cloud security concepts. They allow you to build experience in cloud security before selecting the right exam for you. Gaining a cloud security certification is a valuable step toward entering the field of cloud security services. When choosing which certification to pursue, make sure to align them with your short-term and long-term career objectives.
We have provided everything in the blog. Now you must take the right step and move ahead for superior career progress. All the best!
Get ready to qualify CCSK and CCSP exam with real-time exam questions expert guidance. Become Certified Now!

