Securing Amazon Web Services Account with IAM
AWS Identity and Access Management (IAM) offers centralized management of access and authentication of users to the services in an AWS account. The service offers the mechanisms to identify who holds access to an AWS account and to control what they can do with the AWS Cloud services in that AWS account. Note, that the IAM service is provided at no additional charge.
IAM is also integrated with AWS Marketplace so that we can control who in the organization can subscribe to the software and services offered in AWS Marketplace. Since subscribing to certain software in AWS Marketplace launches an Amazon EC2 instance to run the software, this is an important access control feature. The use of IAM to control access to AWS Marketplace also enables AWS account owners to have fine-grained control over usage and software costs.
IAM User
- IAM user is primarily an entity in an AWS account that provides a way to interact with the resources in the account.
- A user can be any individual, system, or application that interacts with AWS resources, either programmatically (using AWS Software Development Kits [SDKs]), through the AWS Management Console, or through the AWS Command Line Interface (AWS CLI).
- When an AWS account is created, the credentials used at account creation become the root user account ID
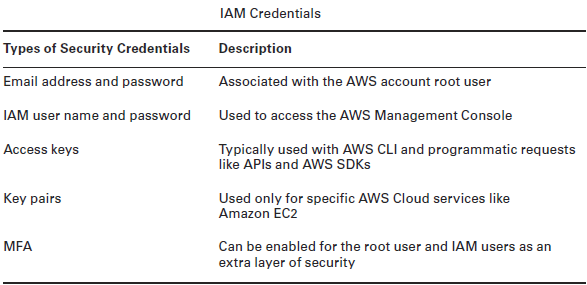
IAM Credentials
primarily there are three ways to use AWS Cloud services and access resources such that these three access mechanisms require credentials, namely –
- AWS Management Console using a web browser
- AWS CLI,
- Next, AWS SDKs through API calls.
How to manage IAM Access Keys?
- Make sure that API requests be signed is required by the AWS. This means that they must include a digital signature that AWS can use to verify the identity of the requestor.
- Also we can calculate the digital signature using a cryptographic hash function. IAM roles provide temporary credentials, which not only automatically load to the target instance, but also automatically rotate multiple times a day.
- The access keys comprise two components –
- Access key ID
- Secret access key
The access key is active by default. Each user can have two active access keys. This enables access keys to rotate without the user temporarily losing access to his AWS account.
The IAM access key can be placed in –
- Linux: ~/.aws/credentials file
- Windows: \%USERPROFILE%\.awscredentials
Here, the root user access keys should not be used. Also the recommended practice is to delete the root user access keys.
Multi-Factor Authentication (MFA)
Now this Multi-Factor Authentication (MFA) adds an additional layer of security when accessing AWS Cloud services. So even before assuming the role as an additional layer of security we would require the user to use MFA. Some of the MFA types supported by the IAM service are –
- Hardware devices (Gemalto)
- Virtual MFA applications (such as Google Authenticator)
- Simple Message Service (SMS) (via mobile devices) can be used for MFA with an AWS account where SMS MFA uses SMS text messaging to verify an IAM user.
IAM Groups
IAM group is a collection of IAM users such that the IAM groups cannot be nested. Here an IAM user can be a member of multiple groups. Such that the permissions for the entire group can be specified. Creating IAM groups and assigning permissions to them is the recommended approach.
IAM Policies
We can define IAM Polices as JSON-formatted permission documents which are used to grant or deny access to IAM users. Here a least privilege approach must be used when assigning permissions so that there are just enough permissions to perform a job or set of tasks. We should only grant the permissions necessary to perform a task. Least privilege reduces the chances of mistakes being made when actions are performed.
An IAM policy consists of four main elements –
- Action
- Effect
- Resource
- Conditions (optional)
IAM Roles
IAM Roles are temporary user credentials. Such that IAM user credentials are regarded as static credentials and static AWS credentials should not be embedded in software source code or placed on Amazon EC2 instances — as there is a chance they could be compromised and used for unauthorized access to resources in an AWS account.
The IAM roles do not have a user name or password associated with them; instead, they have temporary credentials consisting of the following:
- Access key ID
- Secret access key
- Token
- Duration
IAM roles enable temporary credentials to create and issue when needed for the following –
- Applications written with a language-specific AWS SDK
- Amazon EC2 instance access to an AWS resource
- IAM user to gain temporary credentials to undertake a more powerful action (for example, Amazon EC2 instance termination) only when needed
- Federated user accounts
Just as permission documents grant or deny access to IAM users, they grant/deny access to IAM roles.
Best Practices for Securing AWS Account
AWS recommends several best practices for securing an AWS account –
- Require MFA for root-level access.
- Do not share root credentials with anyone other than the account holder.
- Physically secure root account hardware MFA devices in a safe place, such as a vault.
- Create individual IAM users.
- Use groups to assign permissions to IAM users.
- Enable MFA for privileged users.
- Use IAM roles for applications that run on Amazon EC2 instances.
- Delegate by using IAM roles instead of sharing credentials.
- Rotate credentials regularly.
- Remove unnecessary credentials.
- Use policy conditions for extra security.
- Monitor activity on our AWS account.
- Remove root credentials.
- Use access levels to review IAM permissions.
- Using AWS-defined policies to assign permissions whenever possible.
- Use IAM roles to provide cross-account access.
