Auditing report logs in the Azure Active Directory portal
In this we’ll understand about the Azure Active Directory (Azure AD) reports and various concepts of auditing logs reports.
Azure Active Directory
Using Azure Active Directory, you can get the information you need to determine how your environment is doing. However, this reporting architecture consists of the following components:
Activity
- Firstly, this includes the sign-ins report that provides information about the usage of managed applications and user sign-in activities.
- Then, it has Audit logs which provides traceability through logs for all changes done by various features within Azure AD.
Security
- It includes Risky sign-ins, it refers to an indicator for a sign-in attempt that is performed by someone who is not the legitimate owner of a user account.
- Then, it has Users flagged for risk, this is an indicator for a user account that might have been compromised.
Auditing logs
The Azure AD audit logs provide records of system activities for compliance. However, to access the audit report just select Audit logs in the Monitoring section of Azure Active Directory.
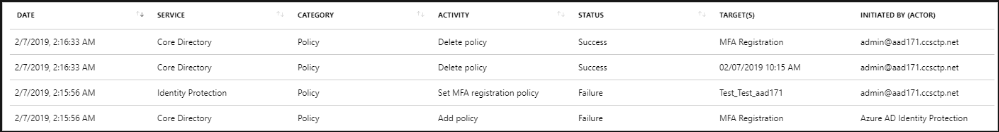
An audit log has a default list view that shows:
- Firstly, the date and time of the occurrence
- Secondly, service that logged the occurrence
- Then, the category and name of the activity (what)
- Fourthly, the status of the activity (success or failure)
- After that, the target
- Lastly, initiator/actor (who) of an activity
Filtering audit logs
Auditing data logs filtering can be done on the following fields:
- Service
- Category
- Activity
- Status
- Target
- Date range
- Audit logs
Types of Filter
There are various types of filters in the Audit logs. Let’s define them,
Firstly, the Service filter which allows you to select from a drop-down list of the following services:
- Firstly, All, AAD Management UX, Access Reviews, Account Provisioning, Application Proxy, and Authentication Methods
- Secondly, B2C, Conditional Access, Core Directory, Entitlement Management, Hybrid Authentication, and Identity Protection
- Then, Invited Users, MIM Service, MyApps, PIM, Self-service Group Management, Self-service Password Management and Terms of Use
Secondly, the Category filter, it enables you to select one of the following filters:
- Firstly, All, AdministrativeUnit, ApplicationManagement, Authentication, and Authorization
- Secondly, Contact, Device, DeviceConfiguration, DirectoryManagement, EntitlementManagement and GroupManagement
- Thirdly, KerberosDomain, KeyManagement, Label, and Others
- After that, PermissionGrantPolicy, Policy, ResourceManagement, RoleManagement and UserManagement
Thirdly, the Activity filter, it is based on the category and activity resource type selection you make. You can select a specific activity you want to see or choose all.
After that, the Status filter which allows you to filter based on the status of an audit operation. The status can be one of the following:
- All
- Success
- Failure
Then, the Target filter, this allows you to search for a particular target by the starting of the name or user principal name (UPN). The target name and UPN are case-sensitive.
Lastly, the Date range filter, which enables you to define a time-frame for the returned data. However, in this the possible values are:
- 7 days
- 24 hours
- Custom
Audit logs shortcuts
In addition to Azure Active Directory, the Azure portal provides you with two additional entry points to audit data:
- Firstly, Users and groups
- Then, Enterprise applications
Users and groups audit logs
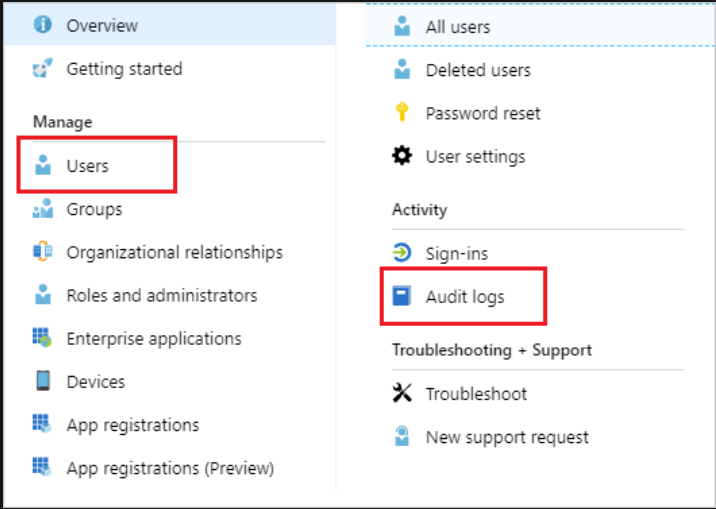
With user and group-based auditing reports, you can get answers to questions such as:
- What types of updates are applied to the users?
- How many users were changed?
- How many passwords were changed?
- What has an administrator done in a directory?
- What are the groups that have been added?
- Are there groups with membership changes?
- Have the owners of the group been changed?
- What licenses have been assigned to a group or a user?
Enterprise applications audit logs
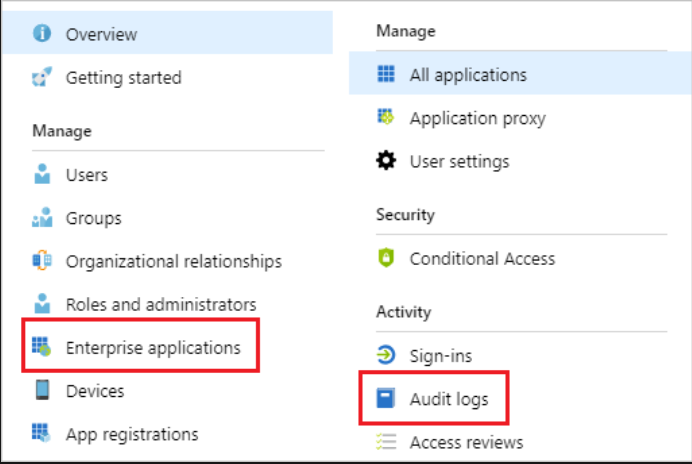
With application-based audit reports, you can get answers to questions such as:
- What is the status of adding and updating applications?
- Is there any removal of any applications?
- Has a service principal for an application changed?
- Is there any change in the names of applications?
- Who gave consent to an application?
Reference: Microsoft Documentation


